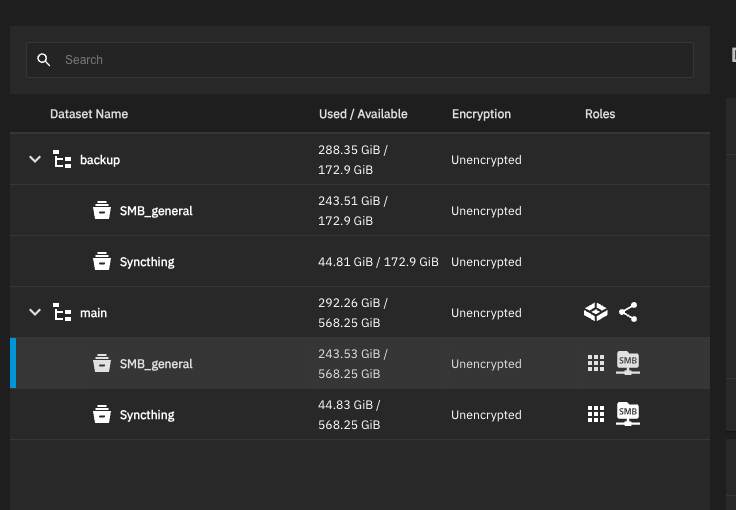
I’m not being pedantic. Understanding the differences between drives, vdevs, pools, datasets, folders, zvols, snapshots, and clones isn’t simply academic. You need to have a grasp on these terms and concepts to minimize mistakes in the future.
This doesn’t make sense. I think you mean “pool”, but then that also doesn’t make sense, since you are replicating datasets.
I won’t dwell on this. I do recommend you take the time to understand the fundamentals of ZFS, even if it won’t play into your current migration task.
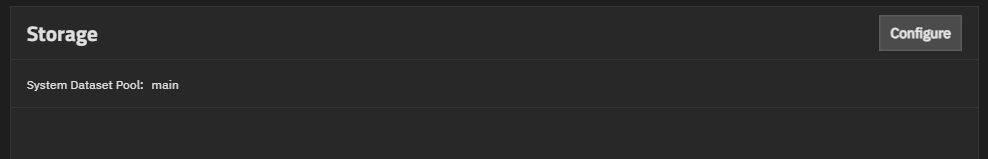
The “System Dataset” is unique to TrueNAS. A “hidden” dataset named .system is nested under the root dataset of whichever pool you select. (It can also be place in the boot-pool instead.) You cannot see the System Dataset in the GUI. (It will, however, inform you which pool holds the System Dataset. Alternatively, you can view it in the command-line, like with any other dataset.)
With Core, you can have the System Dataset encrypted, simply by having the pool’s root dataset encrypted. This allows you to store your syslogs in an encrypted space, and it also decouples your logs from your boot-pool. (Boot drive dies? New install? You get to keep the syslogs.)
Unfortunately, with SCALE (and now “CE”), they removed the ability to choose where the syslogs are saved. 
First of all, do you really need a key? Is there a reason you don’t want to use a passphrase? You can lose a key/keyfile. You can’t “lose” a passphrase, unless you forget it.
There’s also one less thing to worry about backing up and keeping safe: a keyfile. With a passphrase, you never have to remember to “backup” or “verify” a keyfile.
Once the pseudo-root datasets are the state of encryption you want (desired keyfile/passphrase), and once you have the children inherit their respective pseudo-root dataset’s encryption properties, then each “encryptionroot” is all that matters going forward in regards to unlocking and replicating. (In your case, you’ll have a total of 2 encryptionroots. Each pseudo-root dataset will be an encryptionroot.)
If the “Site B” side of “STAGE 0” is the final state of encryption you want (after the children inherit the encryption properties of their respective parents), then you don’t need to mess with inheritance any more. Just don’t replicate any children. Only replicate the pseudo-roots datasets (aka the “encryptionroot” parents.)
You can even use “raw streams” for your replications, in which no unlocking, keys or, passphrases are necessary in order to replicate. The replication will happen “raw”. You’ll still need the key/passphrase to unlock and access the data within, but you can replicate without the need to unlock anything on either end.
EDIT: Please be careful. I recommend using “checkpoints” and to avoid destroying anything, even after a successful replication, until you can confirm it was a success and that you can access your data.
If you have a spare, large USB drive lying around, it doesn’t hurt to create a single-drive pool and do a full replication to it to hold onto everything temporarily, just in case something goes horribly wrong.