First time posting, hoping to reach out to the community. I have actually been a long time user of TrueNas, I had been successfully running Trunas core for almost five years now without an issue. I have only used my nas for storage, iscsi and SMB services, nothing complex like jails or anything.
After upgrade from core to scale, I cannot get the Active Directory integration to work at all.
The error from Scale:
gssapi.raw.exceptions.MissingCredentialsError: Major (458752): No credentials were supplied, or the credentials were unavailable or inaccessible, Minor (2529638926): KDC has no support for encryption type
I can see it makes it to the Windows Domain controller successfully but it is failing with the same error just in Microsoft syntax:
Kerberos pre-authentication failed.
Account Information:
Security ID: <truenasNameRedacted>$
Account Name: $
Service Information:
Service Name: krbtgt/
Network Information:
Client Address:
Client Port: 58960
Additional Information:
Ticket Options: 0x40010010
Failure Code: 0xE
Pre-Authentication Type: 0
An 0xE means: KDC_ERR_ETYPE_NOSUPP KDC has no support for encryption type
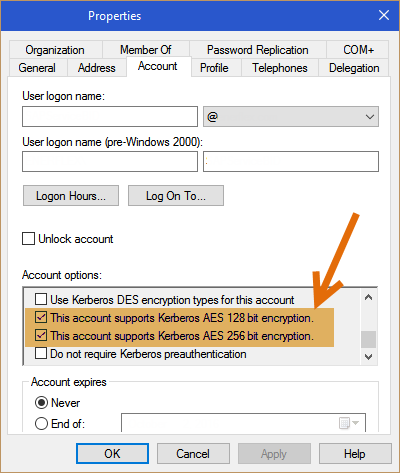
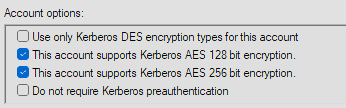
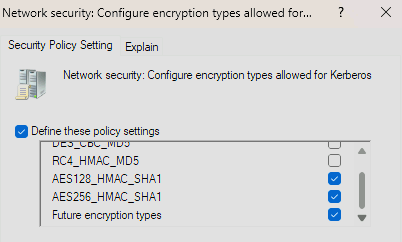
For all of my other lab servers I see the KDC is working just fine, the KDC is issuing tickets on AES 128, AES 256.
The time is in sync with the nas and the domain, they are only maybe 1 to 2 seconds max apart in time. I have also tried adding the encryption types to my “Libdefaults Auxiliary Parameters” with no success, values below.
permitted_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96
default_tgs_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96
default_tkt_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96
To me it seems like the nas isn’t listening to the stronger encryption types and maybe is still trying something not supported by the KDC. I am at a loss of how to ‘force’ it to use the accepted types, all my research suggests it should just use this. I have also tried purging the config but its always the same error.
AD Forest is 2025, all latest updates are deployed to the DCs.
Hopefully someone knows what I need to do to resolve it.