E_B
December 5, 2024, 11:21pm
1
Hello
An email alert from my TN box tells me there’s an update:
“A system update is available. Go to System Settings → Update to download and apply the update”.
but when I try to check via the UI:
I see
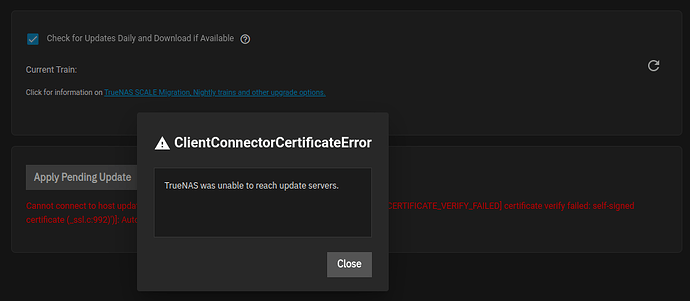
when I press “check for updates” , the writing in red saying
“Cannot connect to host update.ixsystems.com:443 ssl:True [SSLCertVerificationError: (1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate (_ssl.c:992)’)]: Automatic update check failed. Please check system network settings”.
My LAN<-> internet connectivity seems fine and I can’t find anything wrong locally. I’m using Dragonfish-24.04.2. Does the TN s/w server sometimes fail, perhaps?
Same problem here, although my error is ‘hostname mismatch’ on 24.10.0.2.
Looking fine from here on a 24.10.0.2 machine.
root@mini-r[~]# echo | openssl s_client -showcerts -servername update.ixsystems.com -connect update.ixsystems.com:443 2>/dev/null | openssl x509 -inform pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f6:e9:2e:89:59:2d:0e:6e:13:11:ef:55:e1:b7:66:94
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, O = Google Trust Services, CN = WR1
Validity
Not Before: Nov 19 11:42:49 2024 GMT
Not After : Feb 17 11:42:48 2025 GMT
Subject: CN = update.ixsystems.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:45:0f:3f:ba:f2:05:3b:8b:18:1e:01:6f:f4:8f:
88:de:89:c6:1b:51:30:ce:64:1d:ed:d7:f1:a9:52:
28:d7:82:0f:28:5e:a9:f9:a0:35:f2:d1:86:44:07:
25:62:45:e4:44:dc:88:c7:20:8c:33:a5:08:c9:c4:
69:59:91:30:c7
ASN1 OID: prime256v1
NIST CURVE: P-256
Do you have some manner of proxy server or “web filter” software in place?
1 Like
i would try cahing the web-ui to difrent port i use treafik on 443 and 80 so i set my web ui to 444 and 81 hope it owrks
Turns out ControlD was flagging (the update dot ixsystems dot com domain I’m not allowed to name in this comment) as malware. I’ve bypassed it for now. Hasn’t been a problem before.
1 Like
sprucegoose:
ControlD
Thanks for the info - and really, they won’t even let you post the URL in a comment? Harsh.
I’ve opened a support ticket with them (under my actual name, of course) and asked them to reach out to me for confirmation. Hopefully we’ll get it unlisted for any other customers in the same scenario.
Thanks. I assume it’s because I’m a new account. Long time lurker, first time poster
1 Like
E_B
December 6, 2024, 9:06am
8
I tried this morning and all is well again (having made no changes to my local network):
so I can only assume the problem was temporary and anyway was (is) external to my network.
(But to answer your question: in terms of local filtering, I have got Adguard running on TN but its DNS blocklists have not altered in the mean time).
edit: I also ran your command as root to see what happens
echo | openssl s_client -showcerts -servername update.ixsystems.com -connect update.ixsystems.com:443 2>/dev/null | openssl x509 -inform pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f6:e9:2e:89:59:2d:0e:6e:13:11:ef:55:e1:b7:66:94
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, O = Google Trust Services, CN = WR1
Validity
Not Before: Nov 19 11:42:49 2024 GMT
Not After : Feb 17 11:42:48 2025 GMT
Subject: CN = update.ixsystems.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:45:0f:3f:ba:f2:05:3b:8b:18:1e:01:6f:f4:8f:
88:de:89:c6:1b:51:30:ce:64:1d:ed:d7:f1:a9:52:
28:d7:82:0f:28:5e:a9:f9:a0:35:f2:d1:86:44:07:
25:62:45:e4:44:dc:88:c7:20:8c:33:a5:08:c9:c4:
69:59:91:30:c7
ASN1 OID: prime256v1
NIST CURVE: P-256
which looks like the same result. All fixed!
The ControlD team was really on top of things, and stated that the false-positive should be gone now. @sprucegoose if you have time, I’d appreciate if you could test without your bypass rule and see if it still lets you through.
Lending further weight to the “it’s always DNS” argument.
1 Like
I disabled the bypass and the malware flagged blocking returned. I’ve reactivated the bypass and it’s working again. It is indeed ‘always DNS’.
I’m in Australia, if that matters.
Same problem. Turned out my Pi-hole was blocking:
update dot ixsystems dot com (blocked link dor storjshare dot io)
Just found the free ControlD Malware DNS is still filtering update dash master dot ixsystems dot com