I tried the following users
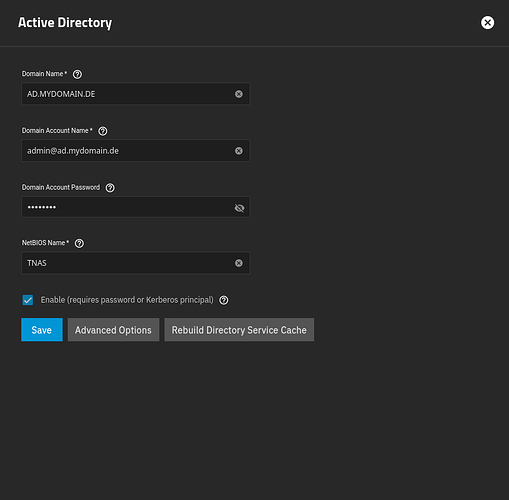
- domain user ‘ldapservices’ shown under Bind DN
- ‘Administrator’
- ‘admin’
- with its corresponding passswords
I always get the error message
'User specified does not have administrator privileges'
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 488, in run
await self.future
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 533, in __run_body
rv = await self.method(*args)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 179, in nf
return await func(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 49, in nf
res = await f(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py", line 576, in do_update
raise e
File "/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py", line 565, in do_update
await self.__start(job)
File "/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py", line 607, in __start
join_resp = await job.wrap(await self.middleware.call(
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 692, in wrap
return await subjob.wait(raise_error=True)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 436, in wait
raise self.exc_info[1]
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 488, in run
await self.future
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 535, in __run_body
rv = await self.middleware.run_in_thread(self.method, *args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1364, in run_in_thread
return await self.run_in_executor(io_thread_pool_executor, method, *args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1361, in run_in_executor
return await loop.run_in_executor(pool, functools.partial(method, *args, **kwargs))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3.11/concurrent/futures/thread.py", line 58, in run
result = self.fn(*self.args, **self.kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/utils/directoryservices/krb5.py", line 331, in check_ticket
return fn(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/join.py", line 244, in join_domain
do_join_fn(job, ds_type, domain)
File "/usr/lib/python3/dist-packages/middlewared/utils/directoryservices/krb5.py", line 331, in check_ticket
return fn(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/activedirectory_join_mixin.py", line 359, in _ad_join
self._ad_join_impl(job, ad_config)
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/activedirectory_join_mixin.py", line 285, in _ad_join_impl
raise CallError(err_msg)
middlewared.service_exception.CallError: [EFAULT] Current debug levels:
all: 5
tdb: 5
printdrivers: 5
lanman: 5
smb: 5
rpc_parse: 5
rpc_srv: 5
rpc_cli: 5
passdb: 5
sam: 5
auth: 5
winbind: 5
vfs: 5
idmap: 5
quota: 5
acls: 5
locking: 5
msdfs: 5
dmapi: 5
registry: 5
scavenger: 5
dns: 5
ldb: 5
tevent: 5
auth_audit: 5
auth_json_audit: 5
kerberos: 5
drs_repl: 5
smb2: 5
smb2_credits: 5
dsdb_audit: 5
dsdb_json_audit: 5
dsdb_password_audit: 5
dsdb_password_json_audit: 5
dsdb_transaction_audit: 5
dsdb_transaction_json_audit: 5
dsdb_group_audit: 5
dsdb_group_json_audit: 5
lp_load_ex: refreshing parameters
Initialising global parameters
rlimit_max: increasing rlimit_max (1024) to minimum Windows limit (16384)
INFO: Current debug levels:
all: 5
tdb: 5
printdrivers: 5
lanman: 5
smb: 5
rpc_parse: 5
rpc_srv: 5
rpc_cli: 5
passdb: 5
sam: 5
auth: 5
winbind: 5
vfs: 5
idmap: 5
quota: 5
acls: 5
locking: 5
msdfs: 5
dmapi: 5
registry: 5
scavenger: 5
dns: 5
ldb: 5
tevent: 5
auth_audit: 5
auth_json_audit: 5
kerberos: 5
drs_repl: 5
smb2: 5
smb2_credits: 5
dsdb_audit: 5
dsdb_json_audit: 5
dsdb_password_audit: 5
dsdb_password_json_audit: 5
dsdb_transaction_audit: 5
dsdb_transaction_json_audit: 5
dsdb_group_audit: 5
dsdb_group_json_audit: 5
Processing section "[global]"
doing parameter disable spoolss = True
doing parameter dns proxy = False
doing parameter load printers = False
doing parameter max log size = 5120
doing parameter printcap = /dev/null
doing parameter bind interfaces only = True
doing parameter fruit:nfs_aces = False
doing parameter fruit:zero_file_id = False
doing parameter restrict anonymous = 2
doing parameter winbind request timeout = 60
doing parameter passdb backend = tdbsam:/var/run/samba-cache/private/passdb.tdb
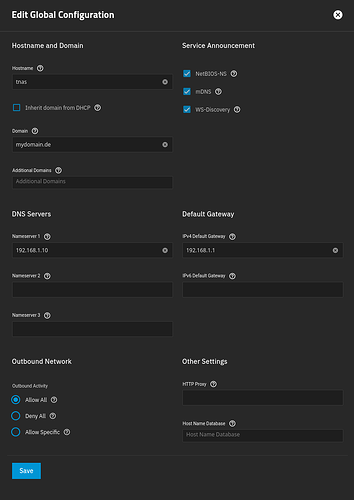
doing parameter workgroup = mydomain
doing parameter netbios name = TNAS
doing parameter netbios aliases =
doing parameter guest account = nobody
doing parameter obey pam restrictions = False
doing parameter create mask = 0664
doing parameter directory mask = 0775
doing parameter ntlm auth = False
doing parameter server multichannel support = False
doing parameter unix charset = UTF-8
doing parameter local master = False
doing parameter server string = TrueNAS Server
doing parameter log level = 1
doing parameter logging = file
doing parameter server smb encrypt = default
doing parameter server role = member server
doing parameter kerberos method = secrets and keytab
doing parameter security = ADS
doing parameter domain master = False
doing parameter preferred master = False
doing parameter winbind cache time = 7200
doing parameter winbind max domain connections = 10
doing parameter winbind use default domain = False
doing parameter client ldap sasl wrapping = seal
doing parameter template shell = /bin/sh
doing parameter allow trusted domains = False
doing parameter realm = AD.mydomain.DE
doing parameter ads dns update = False
Unknown parameter encountered: "ads dns update"
Ignoring unknown parameter "ads dns update"
doing parameter winbind nss info = template
doing parameter template homedir = /var/empty
doing parameter winbind enum users = True
doing parameter winbind enum groups = True
doing parameter idmap config mydomain : backend = rid
doing parameter idmap config mydomain : range = 100000001 - 200000000
doing parameter idmap config * : backend = tdb
doing parameter idmap config * : range = 90000001 - 100000000
doing parameter registry shares = True
doing parameter include = registry
doing parameter registry shares = yes
process_registry_service: service name global
pm_process() returned Yes
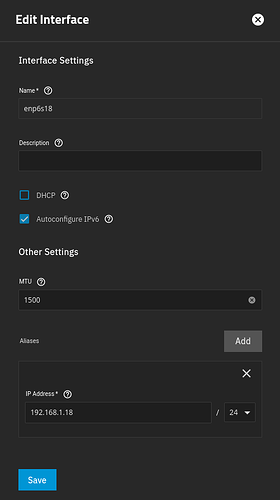
added interface enp6s18 ip=fd0b:59a:8dc2:0:be24:11ff:fef3:7c35 bcast= netmask=ffff:ffff:ffff:ffff::
added interface enp6s18 ip=fdb3:74c4:a1c6:0:be24:11ff:fef3:7c35 bcast= netmask=ffff:ffff:ffff:ffff::
added interface enp6s18 ip=192.168.1.18 bcast=192.168.1.255 netmask=255.255.255.0
Registering messaging pointer for type 2 - private_data=(nil)
register_msg_pool_usage: Registered MSG_REQ_POOL_USAGE
Registering messaging pointer for type 11 - private_data=(nil)
Registering messaging pointer for type 12 - private_data=(nil)
Registered MSG_REQ_DMALLOC_MARK and LOG_CHANGED
Registering messaging pointer for type 1 - private_data=(nil)
Registering messaging pointer for type 5 - private_data=(nil)
Registering messaging pointer for type 51 - private_data=(nil)
added interface enp6s18 ip=fd0b:59a:8dc2:0:be24:11ff:fef3:7c35 bcast= netmask=ffff:ffff:ffff:ffff::
added interface enp6s18 ip=fdb3:74c4:a1c6:0:be24:11ff:fef3:7c35 bcast= netmask=ffff:ffff:ffff:ffff::
added interface enp6s18 ip=192.168.1.18 bcast=192.168.1.255 netmask=255.255.255.0
libnet_Join:
libnet_JoinCtx: struct libnet_JoinCtx
in: struct libnet_JoinCtx
dc_name : NULL
machine_name : 'TNAS'
domain_name : *
domain_name : 'AD.mydomain.DE'
domain_name_type : JoinDomNameTypeDNS (1)
account_ou : NULL
admin_account : 'smbadmin'
admin_domain : NULL
machine_password : NULL
join_flags : 0x00000023 (35)
0: WKSSVC_JOIN_FLAGS_IGNORE_UNSUPPORTED_FLAGS
0: WKSSVC_JOIN_FLAGS_JOIN_WITH_NEW_NAME
0: WKSSVC_JOIN_FLAGS_JOIN_DC_ACCOUNT
0: WKSSVC_JOIN_FLAGS_DEFER_SPN
0: WKSSVC_JOIN_FLAGS_MACHINE_PWD_PASSED
0: WKSSVC_JOIN_FLAGS_JOIN_UNSECURE
1: WKSSVC_JOIN_FLAGS_DOMAIN_JOIN_IF_JOINED
0: WKSSVC_JOIN_FLAGS_WIN9X_UPGRADE
0: WKSSVC_JOIN_FLAGS_ACCOUNT_DELETE
1: WKSSVC_JOIN_FLAGS_ACCOUNT_CREATE
1: WKSSVC_JOIN_FLAGS_JOIN_TYPE
os_version : NULL
os_name : NULL
os_servicepack : NULL
create_upn : 0x00 (0)
upn : NULL
dnshostname : NULL
modify_config : 0x00 (0)
ads : NULL
debug : 0x01 (1)
use_kerberos : 0x01 (1)
secure_channel_type : SEC_CHAN_WKSTA (2)
desired_encryption_types : 0x0000001c (28)
provision_computer_account_only: 0x00 (0)
odj_provision_data : NULL
request_offline_join : 0x00 (0)
Opening cache file at /var/run/samba-lock/gencache.tdb
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
dns_rr_srv_fill_done: async DNS A lookup for dc1.ad.mydomain.de [0] got dc1.ad.mydomain.de -> 192.168.1.10
dns_rr_srv_fill_done: async DNS AAAA lookup for dc1.ad.mydomain.de returned 0 addresses.
saf_fetch: Returning "dc1.ad.mydomain.de" for "AD.mydomain.DE" domain
get_dc_list: preferred server list: "dc1.ad.mydomain.de, *"
resolve_ads: Attempting to resolve KDCs for AD.mydomain.DE using DNS
dns_rr_srv_fill_done: async DNS A lookup for dc1.ad.mydomain.de [0] got dc1.ad.mydomain.de -> 192.168.1.10
dns_rr_srv_fill_done: async DNS AAAA lookup for dc1.ad.mydomain.de returned 0 addresses.
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
get_dc_list: returning 1 ip addresses in an ordered list
get_dc_list: 192.168.1.10
saf_fetch: Returning "dc1.ad.mydomain.de" for "AD.mydomain.DE" domain
get_dc_list: preferred server list: "dc1.ad.mydomain.de, *"
resolve_ads: Attempting to resolve KDCs for AD.mydomain.DE using DNS
dns_rr_srv_fill_done: async DNS A lookup for dc1.ad.mydomain.de [0] got dc1.ad.mydomain.de -> 192.168.1.10
dns_rr_srv_fill_done: async DNS AAAA lookup for dc1.ad.mydomain.de returned 0 addresses.
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
get_dc_list: returning 1 ip addresses in an ordered list
get_dc_list: 192.168.1.10
create_local_private_krb5_conf_for_domain: wrote file /var/run/samba-lock/smb_krb5/krb5.conf._JOIN_ with realm AD.mydomain.DE KDC list:
kdc = 192.168.1.10
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
Connecting to 192.168.1.10 at port 445
socket options: SO_KEEPALIVE=0, SO_REUSEADDR=0, SO_BROADCAST=0, TCP_NODELAY=1, TCP_KEEPCNT=9, TCP_KEEPIDLE=7200, TCP_KEEPINTVL=75, IPTOS_LOWDELAY=0, IPTOS_THROUGHPUT=0, SO_REUSEPORT=0, SO_SNDBUF=87040, SO_RCVBUF=131072, SO_SNDLOWAT=1, SO_RCVLOWAT=1, SO_SNDTIMEO=0, SO_RCVTIMEO=0, TCP_QUICKACK=1, TCP_DEFER_ACCEPT=0, TCP_USER_TIMEOUT=0
cli_session_setup_spnego_send: Connect to dc1.ad.mydomain.de as smbadmin@AD.mydomain.DE using SPNEGO
GENSEC backend 'gssapi_spnego' registered
GENSEC backend 'gssapi_krb5' registered
GENSEC backend 'gssapi_krb5_sasl' registered
GENSEC backend 'spnego' registered
GENSEC backend 'schannel' registered
GENSEC backend 'ncalrpc_as_system' registered
GENSEC backend 'sasl-EXTERNAL' registered
GENSEC backend 'ntlmssp' registered
GENSEC backend 'ntlmssp_resume_ccache' registered
GENSEC backend 'http_basic' registered
GENSEC backend 'http_ntlm' registered
GENSEC backend 'http_negotiate' registered
Starting GENSEC mechanism spnego
Starting GENSEC submechanism gse_krb5
signed SMB2 message (sign_algo_id=2)
signed SMB2 message (sign_algo_id=2)
Bind RPC Pipe: host dc1.ad.mydomain.de auth_type 0, auth_level 1
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 52
check_bind_response: accepted!
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 236
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
signed SMB2 message (sign_algo_id=2)
saf_fetch: Returning "dc1.ad.mydomain.de" for "ad.mydomain.de" domain
get_dc_list: preferred server list: "dc1.ad.mydomain.de, *"
resolve_ads: Attempting to resolve KDCs for ad.mydomain.de using DNS
dns_rr_srv_fill_done: async DNS A lookup for dc1.ad.mydomain.de [0] got dc1.ad.mydomain.de -> 192.168.1.10
dns_rr_srv_fill_done: async DNS AAAA lookup for dc1.ad.mydomain.de returned 0 addresses.
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
get_dc_list: returning 1 ip addresses in an ordered list
get_dc_list: 192.168.1.10
saf_fetch: Returning "dc1.ad.mydomain.de" for "ad.mydomain.de" domain
get_dc_list: preferred server list: "dc1.ad.mydomain.de, *"
resolve_ads: Attempting to resolve KDCs for ad.mydomain.de using DNS
dns_rr_srv_fill_done: async DNS A lookup for dc1.ad.mydomain.de [0] got dc1.ad.mydomain.de -> 192.168.1.10
dns_rr_srv_fill_done: async DNS AAAA lookup for dc1.ad.mydomain.de returned 0 addresses.
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
get_dc_list: returning 1 ip addresses in an ordered list
get_dc_list: 192.168.1.10
create_local_private_krb5_conf_for_domain: wrote file /var/run/samba-lock/smb_krb5/krb5.conf.mydomain with realm AD.mydomain.DE KDC list:
kdc = 192.168.1.10
sitename_fetch: Returning sitename for realm 'AD.mydomain.DE': "Default-First-Site-Name"
namecache_fetch: name dc1.ad.mydomain.de#20 found.
ads_try_connect: ads_try_connect: sending CLDAP request to 192.168.1.10 (realm: ad.mydomain.de)
Successfully contacted LDAP server 192.168.1.10
Connecting to 192.168.1.10 at port 389
Connected to LDAP server dc1.ad.mydomain.de
KDC time offset is 1 seconds
Found SASL mechanism GSS-SPNEGO
ads_sasl_spnego_bind: got OID=1.2.840.48018.1.2.2
ads_sasl_spnego_bind: got OID=1.2.840.113554.1.2.2
ads_sasl_spnego_bind: got OID=1.3.6.1.4.1.311.2.2.10
Starting GENSEC mechanism spnego
Starting GENSEC submechanism gse_krb5
ads_gen_add: AD LDAP: Adding cn=TNAS,CN=Computers,dc=AD,dc=mydomain,dc=DE
ads_print_error: AD LDAP ERROR: 50 (Insufficient access): acl: unable to get access to CN=TNAS,CN=Computers,DC=ad,DC=mydomain,DC=de
libnet_join_precreate_machine_acct: Failed to create machine account
libnet_DomainJoin: Failed to pre-create account in OU CN=Computers,dc=AD,dc=mydomain,dc=DE: Insufficient access
signed SMB2 message (sign_algo_id=2)
Bind RPC Pipe: host dc1.ad.mydomain.de auth_type 0, auth_level 1
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 52
check_bind_response: accepted!
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 40
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
rpc_api_pipe: host dc1.ad.mydomain.de
signed SMB2 message (sign_algo_id=2)
rpc_read_send: data_to_read: 32
signed SMB2 message (sign_algo_id=2)
signed SMB2 message (sign_algo_id=2)
libnet_Join:
libnet_JoinCtx: struct libnet_JoinCtx
out: struct libnet_JoinCtx
odj_provision_data : NULL
account_name : 'TNAS$'
netbios_domain_name : 'mydomain'
dns_domain_name : 'ad.mydomain.de'
forest_name : 'ad.mydomain.de'
dn : NULL
domain_guid : 3c94e9a0-d8c1-46ed-bc42-7e1f402215ed
domain_sid : *
domain_sid : S-1-5-21-3826593470-3054354668-3598288492
modified_config : 0x00 (0)
error_string : 'User specified does not have administrator privileges'
domain_is_ad : 0x01 (1)
set_encryption_types : 0x00000000 (0)
krb5_salt : NULL
dcinfo : *
dcinfo: struct netr_DsRGetDCNameInfo
dc_unc : *
dc_unc : '\\dc1.ad.mydomain.de'
dc_address : *
dc_address : '\\192.168.1.10'
dc_address_type : DS_ADDRESS_TYPE_INET (1)
domain_guid : 3c94e9a0-d8c1-46ed-bc42-7e1f402215ed
domain_name : *
domain_name : 'ad.mydomain.de'
forest_name : *
forest_name : 'ad.mydomain.de'
dc_flags : 0xe00013fd (3758101501)
1: NBT_SERVER_PDC
1: NBT_SERVER_GC
1: NBT_SERVER_LDAP
1: NBT_SERVER_DS
1: NBT_SERVER_KDC
1: NBT_SERVER_TIMESERV
1: NBT_SERVER_CLOSEST
1: NBT_SERVER_WRITABLE
1: NBT_SERVER_GOOD_TIMESERV
0: NBT_SERVER_NDNC
0: NBT_SERVER_SELECT_SECRET_DOMAIN_6
1: NBT_SERVER_FULL_SECRET_DOMAIN_6
0: NBT_SERVER_ADS_WEB_SERVICE
0: NBT_SERVER_DS_8
0: NBT_SERVER_DS_9
0: NBT_SERVER_DS_10
1: NBT_SERVER_HAS_DNS_NAME
1: NBT_SERVER_IS_DEFAULT_NC
1: NBT_SERVER_FOREST_ROOT
dc_site_name : *
dc_site_name : 'Default-First-Site-Name'
client_site_name : *
client_site_name : 'Default-First-Site-Name'
account_rid : 0x00000000 (0)
result : WERR_ACCESS_DENIED
return code = -1
Freeing parametrics: