You’d think so, but the documentation is totally silent on this.
Also, the documentation doesn’t mention that you need Zone.DNS and Zone.Zone permissions so you have to add the Zone.Zone to the template.
You have it right when you see this:
You’d think so, but the documentation is totally silent on this.
Also, the documentation doesn’t mention that you need Zone.DNS and Zone.Zone permissions so you have to add the Zone.Zone to the template.
You have it right when you see this:
It does, but the nonsensical default is to wait until the cert is within 10 days of expiration, so you’ll get a warning from Let’s Encrypt. When you issue the cert, you can change that, and you should really set it to 30 days instead.
You can change the 10 days to 30 days where? In the Scale GUI?
Yes, where you request the certificate. Click the wrench here:
It’s a dumb default in what’s a pretty dumb process, but it isn’t hard to change it.
what is the “pending” CSR? I got the cert loaded up in my certificates section manually, and it is a mystery as to why that “pending” CSR is still visible?
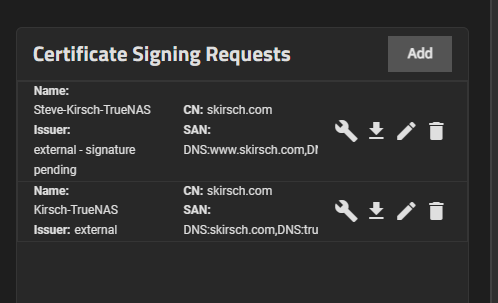
“Pending” really isn’t a very good word choice there, but it’s by design that the CSR remains exposed in the GUI. I don’t know why it’s designed that way[1], but that’s the design.
I suspect it’s because the ACME thing was just “bolted on” to the existing process, without a whole lot of attention given to whether that process made sense with ACME ↩︎
I did find it really odd that I had to get a cloudflare account and supply the API token.
I installed acme on my nginx server running inside the truenas jail and it just uses certbot to get the cert. No need to supply DNS zone credentials.
I guess ix didn’t want to use certbot and did it the quick way?
Using DNS zone credentials means you don’t have to expose the acme host to the internet on port 80.
And for people like me behind CGNAT, I can’t expose a port anyway.
THAT explains it. Thank you!