Sorry in advance for the novel. I’m trying to answer the following 3 questions and I hope it’s not too confusing
- How did my Host encryption key change?
- Why is my Host encryption key different from my backup pool encryption key?
- Why do I need to provide my host key to unlock the root dataset of my usb backup pool?
Defining some terms and process first. This might explain the behaviors I see
-
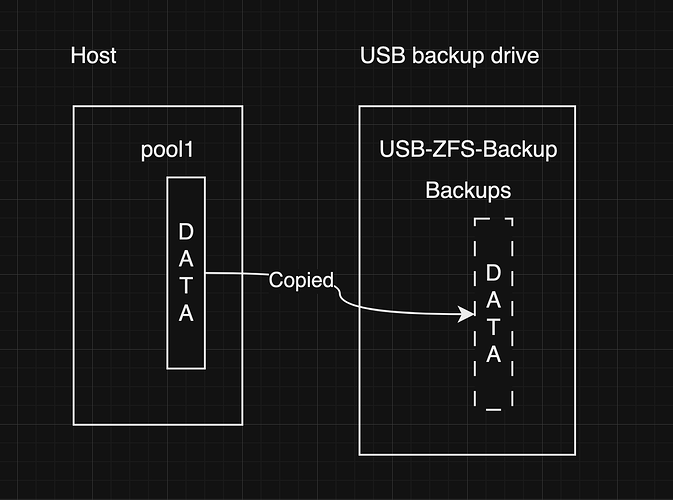
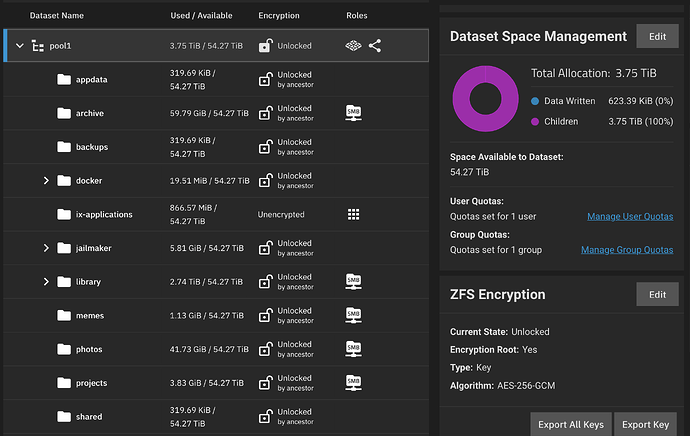
My host pool is called
pool1. -
pool1has a bunch of child datasets and folders holding my data. -
I have a replication task that backs up
pool1to a USB drive. -
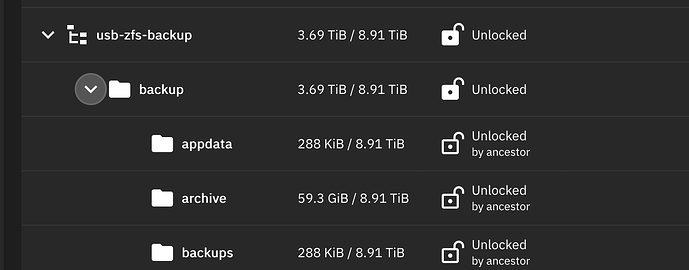
The USB drive pool is called
USB-ZFS-BACKUP. -
USB-ZFS-BACKUPhas a root dataset calledBackups, -
pool1children get written tobackupsdataset on the USB drive.
(See the pic that outlines this. curious if this ultimately explains the following issues)
Ok, now my problem:
This post is semi-related to a previous issue where I needed to manually paste encryption keys to decrypt my usb backup pool.
I was having that issue again, but this time the USB encryption key (Z in the below table) wasn’t working to decrypt the usb root dataset (Backups). I actually found I needed to provide the host encryption key( Y) to decrypt Backups. This surprised me. I thought Z would decrypt everything – whether having to manually paste it or not.
Along the way I decided to export and compare my truenas keys with some earlier key exports. Here’s a table to summarize what I found
| Host Pool (one key / all keys) | Backup Pool(one key / all keys) | |
|---|---|---|
| Last week’s keys | Y / X | Z / Z |
| This week’s keys | Y / Y | Z / Z |
Observations and questions
-
The encryption key for my usb backup is entirely different from my host key. Is this expected?
-
The encryption key for my Host pool somehow changed last week from X to Y depending on whether I had exported a single key or all keys. I have no idea why my host key changed. The timestamp on the 'All keys" and “single key” json file is 5 minutes apart. I don’t remember doing anything that would have changed the key. How is this possible?
-
The process of unlocking my USB drive pool and its root-level dataset (
Backups) required using the USB encryption keyZand then my host encryption keyY, respectively. Is this expected?
I would have expected that decrypting my USB backup pool would ONLY require the Z key. But maybe there’s something about how I wrote pool1 children content into the backups dataset meant the encryption key was inherited and so there are two different keys to use?
I hope this isn’t too confusing - it’s taken be a bit to write this up as plainly as I can. Happy to provide additional details if any of this is unclear. I’m scracthing my head over this.
paging @winnielinnie in case you can shed some light on this.