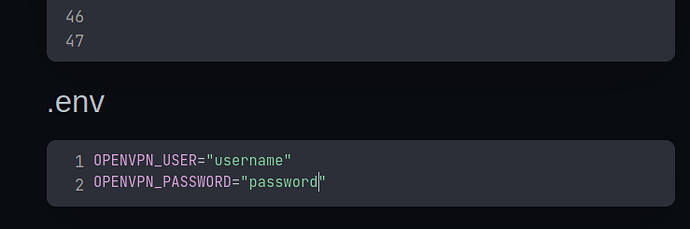
yea i tried 
jack@TruenasScale ~ $ sudo docker run -it --rm --cap-add=NET_ADMIN -e VPN_SERVICE_PROVIDER=custom -e VPN_TYPE=openvpn -v /mnt/basepool/aplications/gluetun/config.ovpn:/gluetun/config.ovpn:ro -e OPENVPN_CUSTOM_CONFIG=/gluetun/config.ovpn -e OPENVPN_USER=xxxxxx -e OPENVPN_PASSWORD=xxxxxx qmcgaw/gluetun
========================================
========================================
=============== gluetun ================
========================================
=========== Made with ❤ by ============
======= https://github.com/qdm12 =======
========================================
========================================
Running version latest built on 2024-12-27T20:18:46.989Z (commit 61b053f)
🔧 Need help? ☕ Discussion? https://github.com/qdm12/gluetun/discussions/new/choose
🐛 Bug? ✨ New feature? https://github.com/qdm12/gluetun/issues/new/choose
💻 Email? quentin.mcgaw@gmail.com
💰 Help me? https://www.paypal.me/qmcgaw https://github.com/sponsors/qdm12
2025-01-02T19:00:20Z INFO [routing] default route found: interface eth0, gateway 172.16.0.1, assigned IP 172.16.0.2 and family v4
2025-01-02T19:00:20Z INFO [routing] local ethernet link found: eth0
2025-01-02T19:00:20Z INFO [routing] local ipnet found: 172.16.0.0/24
2025-01-02T19:00:20Z INFO [firewall] enabling...
2025-01-02T19:00:20Z INFO [firewall] enabled successfully
2025-01-02T19:00:20Z INFO [storage] creating /gluetun/servers.json with 20776 hardcoded servers
2025-01-02T19:00:20Z INFO Alpine version: 3.20.3
2025-01-02T19:00:20Z INFO OpenVPN 2.5 version: 2.5.10
2025-01-02T19:00:20Z INFO OpenVPN 2.6 version: 2.6.11
2025-01-02T19:00:20Z INFO IPtables version: v1.8.10
2025-01-02T19:00:20Z INFO Settings summary:
├── VPN settings:
| ├── VPN provider settings:
| | ├── Name: custom
| | └── Server selection settings:
| | ├── VPN type: openvpn
| | └── OpenVPN server selection settings:
| | ├── Protocol: UDP
| | └── Custom configuration file: /gluetun/config.ovpn
| └── OpenVPN settings:
| ├── OpenVPN version: 2.6
| ├── User: [set]
| ├── Password: [set]
| ├── Custom configuration file: /gluetun/config.ovpn
| ├── Network interface: tun0
| ├── Run OpenVPN as: root
| └── Verbosity level: 1
├── DNS settings:
| ├── Keep existing nameserver(s): no
| ├── DNS server address to use: 127.0.0.1
| └── DNS over TLS settings:
| ├── Enabled: yes
| ├── Update period: every 24h0m0s
| ├── Upstream resolvers:
| | └── cloudflare
| ├── Caching: yes
| ├── IPv6: no
| └── DNS filtering settings:
| ├── Block malicious: yes
| ├── Block ads: no
| ├── Block surveillance: no
| └── Blocked IP networks:
| ├── 127.0.0.1/8
| ├── 10.0.0.0/8
| ├── 172.16.0.0/12
| ├── 192.168.0.0/16
| ├── 169.254.0.0/16
| ├── ::1/128
| ├── fc00::/7
| ├── fe80::/10
| ├── ::ffff:127.0.0.1/104
| ├── ::ffff:10.0.0.0/104
| ├── ::ffff:169.254.0.0/112
| ├── ::ffff:172.16.0.0/108
| └── ::ffff:192.168.0.0/112
├── Firewall settings:
| └── Enabled: yes
├── Log settings:
| └── Log level: info
├── Health settings:
| ├── Server listening address: 127.0.0.1:9999
| ├── Target address: cloudflare.com:443
| ├── Duration to wait after success: 5s
| ├── Read header timeout: 100ms
| ├── Read timeout: 500ms
| └── VPN wait durations:
| ├── Initial duration: 6s
| └── Additional duration: 5s
├── Shadowsocks server settings:
| └── Enabled: no
├── HTTP proxy settings:
| └── Enabled: no
├── Control server settings:
| ├── Listening address: :8000
| ├── Logging: yes
| └── Authentication file path: /gluetun/auth/config.toml
├── Storage settings:
| └── Filepath: /gluetun/servers.json
├── OS Alpine settings:
| ├── Process UID: 1000
| └── Process GID: 1000
├── Public IP settings:
| ├── IP file path: /tmp/gluetun/ip
| ├── Public IP data base API: ipinfo
| └── Public IP data backup APIs:
| ├── ifconfigco
| ├── ip2location
| └── cloudflare
└── Version settings:
└── Enabled: yes
2025-01-02T19:00:21Z INFO [routing] default route found: interface eth0, gateway 172.16.0.1, assigned IP 172.16.0.2 and family v4
2025-01-02T19:00:21Z INFO [routing] adding route for 0.0.0.0/0
2025-01-02T19:00:21Z INFO [firewall] setting allowed subnets...
2025-01-02T19:00:21Z INFO [routing] default route found: interface eth0, gateway 172.16.0.1, assigned IP 172.16.0.2 and family v4
2025-01-02T19:00:21Z INFO TUN device is not available: open /dev/net/tun: no such file or directory; creating it...
2025-01-02T19:00:21Z INFO [dns] using plaintext DNS at address 1.1.1.1
2025-01-02T19:00:21Z INFO [http server] http server listening on [::]:8000
2025-01-02T19:00:21Z INFO [healthcheck] listening on 127.0.0.1:9999
2025-01-02T19:00:21Z INFO [firewall] allowing VPN connection...
2025-01-02T19:00:21Z INFO [openvpn] DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305). OpenVPN ignores --cipher for cipher negotiations.
2025-01-02T19:00:21Z INFO [openvpn] OpenVPN 2.6.11 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
2025-01-02T19:00:21Z INFO [openvpn] library versions: OpenSSL 3.3.2 3 Sep 2024, LZO 2.10
2025-01-02T19:00:21Z INFO [openvpn] TCP/UDP: Preserving recently used remote address: [AF_INET]185.107.94.249:1194
2025-01-02T19:00:21Z INFO [openvpn] UDPv4 link local: (not bound)
2025-01-02T19:00:21Z INFO [openvpn] UDPv4 link remote: [AF_INET]185.107.94.249:1194
2025-01-02T19:00:26Z INFO [openvpn] [vpn-nl.premiumize.me] Peer Connection Initiated with [AF_INET]185.107.94.249:1194
2025-01-02T19:00:26Z ERROR [openvpn] AUTH: Received control message: AUTH_FAILED
Your credentials might be wrong 🤨
2025-01-02T19:00:26Z INFO [openvpn] SIGUSR1[soft,auth-failure] received, process restarting
2025-01-02T19:00:27Z INFO [healthcheck] program has been unhealthy for 6s: restarting VPN (healthcheck error: dialing: dial tcp4: lookup cloudflare.com on 1.1.1.1:53: write udp 172.16.0.2:35123->1.1.1.1:53: write: operation not permitted)
2025-01-02T19:00:27Z INFO [healthcheck] 👉 See https://github.com/qdm12/gluetun-wiki/blob/main/faq/healthcheck.md
2025-01-02T19:00:27Z INFO [healthcheck] DO NOT OPEN AN ISSUE UNLESS YOU READ AND TRIED EACH POSSIBLE SOLUTION
2025-01-02T19:00:27Z INFO [vpn] stopping
2025-01-02T19:00:27Z INFO [vpn] starting
2025-01-02T19:00:27Z INFO [firewall] allowing VPN connection...
2025-01-02T19:00:27Z INFO [openvpn] DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305). OpenVPN ignores --cipher for cipher negotiations.
2025-01-02T19:00:27Z INFO [openvpn] OpenVPN 2.6.11 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
2025-01-02T19:00:27Z INFO [openvpn] library versions: OpenSSL 3.3.2 3 Sep 2024, LZO 2.10
2025-01-02T19:00:27Z INFO [openvpn] TCP/UDP: Preserving recently used remote address: [AF_INET]185.107.94.249:1194
2025-01-02T19:00:27Z INFO [openvpn] UDPv4 link local: (not bound)
2025-01-02T19:00:27Z INFO [openvpn] UDPv4 link remote: [AF_INET]185.107.94.249:1194
2025-01-02T19:00:27Z INFO [openvpn] [vpn-nl.premiumize.me] Peer Connection Initiated with [AF_INET]185.107.94.249:1194
2025-01-02T19:00:27Z ERROR [openvpn] AUTH: Received control message: AUTH_FAILED
Your credentials might be wrong 🤨
2025-01-02T19:00:27Z INFO [openvpn] SIGUSR1[soft,auth-failure] received, process restarting
^C
2025-01-02T19:00:29Z WARN Caught OS signal interrupt, shutting down
2025-01-02T19:00:29Z INFO updater ticker: terminated ✔
2025-01-02T19:00:29Z INFO dns ticker: terminated ✔
2025-01-02T19:00:29Z INFO http server: terminated ✔
2025-01-02T19:00:29Z INFO control: terminated ✔
2025-01-02T19:00:29Z INFO updater: terminated ✔
2025-01-02T19:00:29Z INFO tickers: terminated ✔
2025-01-02T19:00:29Z WARN HTTP health server: goroutine shutdown timed out: after 400ms ⚠
2025-01-02T19:00:29Z INFO vpn: terminated ✔
2025-01-02T19:00:29Z INFO shadowsocks proxy: terminated ✔
2025-01-02T19:00:29Z INFO http proxy: terminated ✔
2025-01-02T19:00:29Z INFO dns: terminated ✔
2025-01-02T19:00:29Z INFO other: terminated ✔
2025-01-02T19:00:29Z INFO [routing] routing cleanup...
2025-01-02T19:00:29Z INFO [routing] default route found: interface eth0, gateway 172.16.0.1, assigned IP 172.16.0.2 and family v4
2025-01-02T19:00:29Z INFO [routing] deleting route for 0.0.0.0/0
2025-01-02T19:00:29Z WARN Shutdown failed: ordered shutdown timed out: HTTP health server: goroutine shutdown timed out: after 400ms
Credentials are absolutly correct.
on my desktop
❱sudo openvpn --config Downloads/vpn-nl.premiumize.me.ovpn --auth-user-pass credentials.txt
[sudo] password for greg:
2025-01-02 19:12:02 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305). OpenVPN ignores --cipher for cipher negotiations.
2025-01-02 19:12:02 Note: Kernel support for ovpn-dco missing, disabling data channel offload.
2025-01-02 19:12:02 WARNING: file 'credentials.txt' is group or others accessible
2025-01-02 19:12:02 OpenVPN 2.6.12 [git:makepkg/038a94bae57a446c+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO] built on Jul 18 2024
2025-01-02 19:12:02 library versions: OpenSSL 3.4.0 22 Oct 2024, LZO 2.10
2025-01-02 19:12:02 DCO version: N/A
2025-01-02 19:12:02 TCP/UDP: Preserving recently used remote address: [AF_INET]185.107.94.249:1194
2025-01-02 19:12:02 Socket Buffers: R=[212992->212992] S=[212992->212992]
2025-01-02 19:12:02 UDPv4 link local: (not bound)
2025-01-02 19:12:02 UDPv4 link remote: [AF_INET]185.107.94.249:1194
2025-01-02 19:12:02 TLS: Initial packet from [AF_INET]185.107.94.249:1194, sid=a1043458 b20a4cc6
2025-01-02 19:12:02 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2025-01-02 19:12:02 VERIFY OK: depth=2, O=Secure Services, CN=Root X1
2025-01-02 19:12:02 VERIFY OK: depth=1, O=Secure Services, CN=Intermediate X5
2025-01-02 19:12:02 VERIFY X509NAME OK: CN=vpn-nl.premiumize.me
2025-01-02 19:12:02 VERIFY OK: depth=0, CN=vpn-nl.premiumize.me
2025-01-02 19:12:03 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519
2025-01-02 19:12:03 [vpn-nl.premiumize.me] Peer Connection Initiated with [AF_INET]185.107.94.249:1194
2025-01-02 19:12:03 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
2025-01-02 19:12:03 TLS: tls_multi_process: initial untrusted session promoted to trusted
2025-01-02 19:12:03 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,route-ipv6 ::/3,route-ipv6 2000::/4,route-ipv6 3000::/4,route-ipv6 fc00::/7,dhcp-option DNS 1.1.1.1,dhcp-option DNS 1.0.0.1,block-outside-dns,tun-ipv6,route-gateway 10.8.0.1,topology subnet,ping 50,ping-restart 120,ifconfig-ipv6 fde7:523e:dd18:bf22::1032/64 fde7:523e:dd18:bf22::1,ifconfig 10.8.0.52 255.255.0.0,peer-id 69,cipher AES-256-GCM,protocol-flags cc-exit tls-ekm dyn-tls-crypt,tun-mtu 1500'
2025-01-02 19:12:03 Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:8: block-outside-dns (2.6.12)
2025-01-02 19:12:03 OPTIONS IMPORT: --ifconfig/up options modified
2025-01-02 19:12:03 OPTIONS IMPORT: route options modified
2025-01-02 19:12:03 OPTIONS IMPORT: route-related options modified
2025-01-02 19:12:03 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
2025-01-02 19:12:03 OPTIONS IMPORT: tun-mtu set to 1500
2025-01-02 19:12:03 net_route_v4_best_gw query: dst 0.0.0.0
2025-01-02 19:12:03 net_route_v4_best_gw result: via 192.168.1.1 dev wlp89s0
2025-01-02 19:12:03 ROUTE_GATEWAY 192.168.1.1/255.255.255.0 IFACE=wlp89s0 HWADDR=d0:12:55:2c:19:94
2025-01-02 19:12:03 GDG6: remote_host_ipv6=n/a
2025-01-02 19:12:03 net_route_v6_best_gw query: dst ::
2025-01-02 19:12:03 sitnl_send: rtnl: generic error (-101): Network is unreachable
2025-01-02 19:12:03 ROUTE6: default_gateway=UNDEF
2025-01-02 19:12:03 TUN/TAP device tun0 opened
2025-01-02 19:12:03 net_iface_mtu_set: mtu 1500 for tun0
2025-01-02 19:12:03 net_iface_up: set tun0 up
2025-01-02 19:12:03 net_addr_v4_add: 10.8.0.52/16 dev tun0
2025-01-02 19:12:03 net_iface_mtu_set: mtu 1500 for tun0
2025-01-02 19:12:03 net_iface_up: set tun0 up
2025-01-02 19:12:03 net_addr_v6_add: fde7:523e:dd18:bf22::1032/64 dev tun0
2025-01-02 19:12:03 net_route_v4_add: 185.107.94.249/32 via 192.168.1.1 dev [NULL] table 0 metric -1
2025-01-02 19:12:03 net_route_v4_add: 0.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2025-01-02 19:12:03 net_route_v4_add: 128.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2025-01-02 19:12:03 add_route_ipv6(::/3 -> fde7:523e:dd18:bf22::1 metric -1) dev tun0
2025-01-02 19:12:03 net_route_v6_add: ::/3 via :: dev tun0 table 0 metric -1
2025-01-02 19:12:03 add_route_ipv6(2000::/4 -> fde7:523e:dd18:bf22::1 metric -1) dev tun0
2025-01-02 19:12:03 net_route_v6_add: 2000::/4 via :: dev tun0 table 0 metric -1
2025-01-02 19:12:03 add_route_ipv6(3000::/4 -> fde7:523e:dd18:bf22::1 metric -1) dev tun0
2025-01-02 19:12:03 net_route_v6_add: 3000::/4 via :: dev tun0 table 0 metric -1
2025-01-02 19:12:03 add_route_ipv6(fc00::/7 -> fde7:523e:dd18:bf22::1 metric -1) dev tun0
2025-01-02 19:12:03 net_route_v6_add: fc00::/7 via :: dev tun0 table 0 metric -1
2025-01-02 19:12:03 Initialization Sequence Completed
2025-01-02 19:12:03 Data Channel: cipher 'AES-256-GCM', peer-id: 69
2025-01-02 19:12:03 Timers: ping 50, ping-restart 120
2025-01-02 19:12:03 Protocol options: protocol-flags cc-exit tls-ekm dyn-tls-crypt
2025-01-02 19:12:05 read UDPv4 [EMSGSIZE Path-MTU=1480|EMSGSIZE Path-MTU=1480]: Message too long (fd=3,code=90)
^C2025-01-02 19:13:48 net_route_v4_del: 185.107.94.249/32 via 192.168.1.1 dev [NULL] table 0 metric -1
2025-01-02 19:13:48 net_route_v4_del: 0.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2025-01-02 19:13:48 net_route_v4_del: 128.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2025-01-02 19:13:48 delete_route_ipv6(::/3)
2025-01-02 19:13:48 net_route_v6_del: ::/3 via :: dev tun0 table 0 metric -1
2025-01-02 19:13:48 delete_route_ipv6(2000::/4)
2025-01-02 19:13:48 net_route_v6_del: 2000::/4 via :: dev tun0 table 0 metric -1
2025-01-02 19:13:48 delete_route_ipv6(3000::/4)
2025-01-02 19:13:48 net_route_v6_del: 3000::/4 via :: dev tun0 table 0 metric -1
2025-01-02 19:13:48 delete_route_ipv6(fc00::/7)
2025-01-02 19:13:48 net_route_v6_del: fc00::/7 via :: dev tun0 table 0 metric -1
2025-01-02 19:13:48 Closing TUN/TAP interface
2025-01-02 19:13:48 net_addr_v4_del: 10.8.0.52 dev tun0
2025-01-02 19:13:48 net_addr_v6_del: fde7:523e:dd18:bf22::1032/64 dev tun0
2025-01-02 19:13:49 SIGINT[hard,] received, process exiting
on other terminal:
❱curl ifconfig.me
2a00:1768:6001:1e::4⏎
⎼⎼⎼⎼⎼⎼⎼⎼⎼⎼ /home/greg ⎼⎼⎼⎼⎼⎼⎼⎼⎼⎼
❱curl -4 ifconfig.me
185.107.94.249⏎
⎼⎼⎼⎼⎼⎼⎼⎼⎼⎼ /home/greg ⎼⎼⎼⎼⎼⎼⎼⎼⎼⎼
❱curl ipinfo.io
{
"ip": "185.107.94.249",
"city": "Roosendaal",
"region": "North Brabant",
"country": "NL",
"loc": "51.5308,4.4653",
"org": "AS43350 NForce Entertainment B.V.",
"postal": "4701",
"timezone": "Europe/Amsterdam",
"readme": "https://ipinfo.io/missingauth"
}⏎