An open source, Linux-based, GUI-friendly NAS OS seemed like a good deal to me, so I install TrueNAS SCALE 24.04.2.2 on a newly built machine.
The first thing I noticed was that it didn’t offer anything for boot device encryption. Okay, weird, but maybe CORE does since BSD has GEOM ELI? Reinstalled with CORE and also nope. Very disappointing that this whole software suite doesn’t have any option for boot device encryption, seeing as this has been a standard feature of Linux, BSD, and Veracrypt on Windows for over a decade.
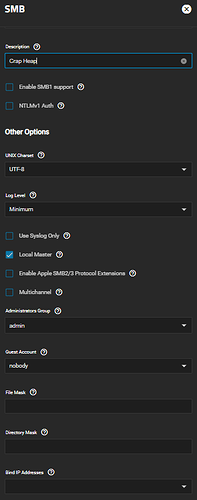
But whatever. I can live without it. Moving on. Set up a dataset (at least that has encryption) and made it an SMB share. Now I see that neither the SMB global config nor the specific share config has anything in the GUI about transport encryption. Whut? Docs here (SMB | TrueNAS Documentation Hub) say it exists, but must be outdated, because the encryption options have been removed from the GUI in the latest version (see pic).
Seems like kind of an important thing to just delete from the GUI, no?
So whatever, I guess security isn’t user-friendly. So I open the shell and try to edit the config file. It’s not there. Whut? Whatever, I’ll create another one. It asks me for a sudo password, which succeeds, and access is denied anyway because I wasn’t allowed to create a root account during the install process.
Can anyone give me any advice on enabling/configuring SMB transit encryption in this OS? I really wanted to like it, but it seems security is just not a priority at iXsystems, so I’m probably gonna just trash it and go with Debian or CentOS instead.
FWIW, the initial install failed at almost every step, too, and required like four hours of debugging. Even the iso download failed the checksum. Twice.
Very unimpressed. Hoping for hope to be restored.