I found this help page at the Resilio site. Everything looks straightforward except for the instruction: “On the Management console generate Agent configuration file sync.conf and put it inside your working pool.” How do I access the Management console?
Resilio Connect is part of their enterprise software suite, whereas Resilio Sync is a different product aimed at SMBs and home users.
I’ve used Resilio Sync for many years, so I’d be happy to help.
Have you already tried using the Resilio Sync app in the official app repository?
Hi and thanks. I have Resilio Sync with a Home Pro license. I used the instructions that I linked to from the Resilio site because I couldn’t find the app in the Truecharts repository. I suppose my biggest problem is that I don’t know how to access a Terminal in Truenas to be able to create directories and files. Is that what is meant by the Management console? (If you hadn’t noticed, I am very new to Truenas ![]()
There isn’t a management console for Resilio Sync and all the required configuration files are generated automatically when you first login to the web interface.
I’m on my phone at the moment but I’ll point you in the right direction once I have a moment.
Basically you would need to create the Resilio Sync container/app yourself by pulling a docker image for it and set some parameters/arguments for it. TrueCharts will no longer be supporting TrueNAS SCALE apps in the next release, so it would be best you don’t use that anyway.
- On the TrueNAS Apps page, click the Custom App button on the top-right.
- Set Application Name to whatever you want - eg. resilio-sync
- In the Image Repository field, paste in lscr.io/linuxserver/resilio-sync
- Add some container environment variables. (press Add button twice). These two refer to the user id and group id of the user who has access to the files for syncing. You must set file permissions ahead of time on your data set. You can check your user id in the TrueNAS users info page. Typically the first user created is 1000, but isn’t always the case.
Environment Variable Name: PUID
Environment Variable Value: 1000
Environment Variable Name: PGID
Environment Variable Value: 1000
- Add External Interfaces for Networking. Add the desired network interface you want to attach and set IPAM type to DHCP.
Add port: 55555 (for the resilio listening port)
Add port: 8888 (for the web UI)
-
Add Host Path Volumes for resilio sync config files. You’ll want to create this ahead of time.
eg.
Host Path: /mnt/tank/docker/resilio-sync/config
Container Path: /config -
Add Host Path for the directories you want to sync, making sure the container path starts with /sync since that directory inside the container is whitelisted by default. It can be changed in sync.conf if you want.
eg.
Host Path: /mnt/tank/myfiles/
Container Path: /sync/mnt/tank/myfiles
I think that should be it. I’ll run a test when I get home.
Be aware, you need some knowledge of how permissions work because without that base knowledge, it can get frustrating.
I’m asking for help. It does not create any configs on the specified path. Accordingly, it does not remember the settings. After restarting the service, no settings are saved. Maybe it needs to put an empty sync.conf file in the specified path? I am grateful in advance for any help.
I never got it working, so decided to wait for the move to Docker in the next Truenas update.
Judging by the number of views, the topic is a success. I need to decide on the choice of storage. Dear developers! Could you tell me how long you will ignore this problem? Do your commercial solutions have the same rejection of resilio sync?
It would sure be a great thing if this was added to the official SCALE catalog…
Solved: Resilio Sync Container on TrueNAS SCALE with working permissions
After two full days of tinkering and testing, I finally figured out how to get Resilio Sync to work on TrueNAS Scale without using a second server with Resilio Sync on it!
and no @Sesos, using this docker container is not great because as stated here
Resilio has deprecated the official docker image in v3.
Environment:
- Dataset: “foo” on TrueNAS SCALE
- Default ownership: user foo and group foo
- Users:
- resilio (ID 3001) is the user running the container (with its PUID/PGID set in Docker) and is a member of group foo.
- SMB-connected computer uses the user foo.
Create Custom App / Docker Settings for Resilio Sync
Below are the critical settings (only changed or configured fields are mentioned):
- Application Name: resilio
- Image/Repository: lscr. io/linuxserver/resilio-sync – No space!.. I had to add a space because I can’t post a link
- Hostname: resilio
- Environment Variables:
- PUID: 3001
- PGID: 3001
- UMASK: 000 – I will later explain why!
- Restart Policy: Unless Stopped
- Network Configuration / Ports:
- Container Port1: 55555
- Host Port1: 55555
- Protocol1: TCP
- Container Port2: 8888
- Host Port2: 8888
- Protocol2: TCP
- Storage Configuration:
- Storage1 Type: ixVolume
- Mount Path: /config
- Dataset Name: resilio_config
- Storage2 Type: Host Path
- Mount Path: /sync/foo
- Enable ACL: checked
- Host Path: /mnt/vault/foo
- ACL Entries:
- ID Type: Entry is for a GROUP
- ID: 3001
- Access: Modify Access
- Force Flag: checked
- Storage1 Type: ixVolume
Scenario & Root Cause:
-
Scenario 1:
When configuring storage for the Resilio Sync container without setting special ACLs, the container (running as resilio) can’t access the “foo” dataset.
Workaround Attempt: You could change the dataset’s permissions so that the owner becomes resilio and group remains foo.
Problem: If you access the dataset via an SMB share (from a computer logged in as foo) and write new files, the new files get created with ownership foo:foo. In that case, Resilio no longer has access because the expected owner is not there. -
Scenario 2:
You might consider adjusting the SMB share configuration to force user and group using parameters like:force user = resilio force group = fooHowever, on TrueNAS SCALE the SMB share settings do not include an “Auxiliary Parameters” option. Moreover, direct modifications to
/etc/smb4.confwon’t persist — they reset on every reboot or SMB service restart.
The Only Realistic (Yet Imperfect) Option:
For this scenario, the only way to have file access work correctly both for Resilio Sync and SMB users would be to have the same user and group for:
- The Resilio container,
- The dataset, and
- The user accessing the SMB share.
This isn’t practical in multiuser environments and compromises security best practices.
How I Solved It:
-
Storage ACL Modification Issue:
Initially, I added ACL settings via the storage configuration as follows:-- Storage2 Type: Host Path -- Storage2 Mount Path: /sync/foo -- Storage2 Enable ACL checked -- Storage2 Host Path: /mnt/vault/foo -- Storage2 ACL Entries: - Storage2 ID Type: Entry is for a GROUP - Storage2 ID: 3001 - Storage2 Access: Modify Access - Storage2 Force Flag checkedHowever, doing this changed the ACL on the dataset, and even when Resilio created or modified files (for example, the
.syncfolder), the ACL was altered so that foo didn’t end up with modify permission. -
Fixing the ACL on the Dataset:
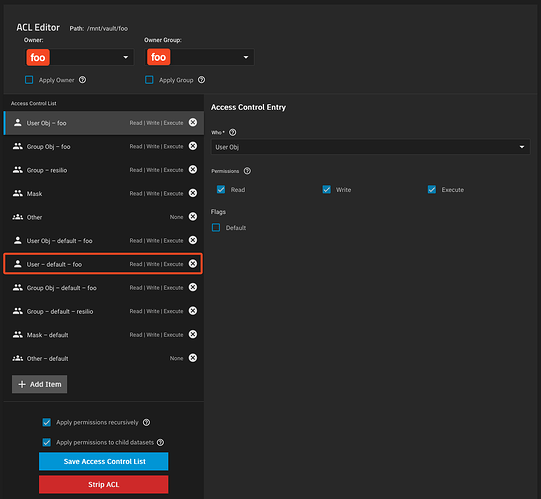
To solve this, I manually changed the ACL of the dataset “foo” to include an ACL entry for user foo with the default flag enabled. The steps were:- Edit the ACL on dataset foo.
- Add an item:
- Who: User
- User: foo
- Permissions: Check Read, Write, and Execute
- Enable Default Flag: checked
- Apply permissions recursively.
- When prompted, confirm the popup warning, then apply permissions to child datasets.
- Save the Access Control List.
Image of what the ACL look like after all the changes
This ensures that even when Resilio creates or modifies files, foo still gets an ACL entry (inherited with default flags) granting full access.
-
Changing the UMASK in the Docker Environment:
Without modifying the UMASK, Resilio uses the default UMASK of 022 which strips write permissions when files are created or modified. This means that even with proper ACL entries, files created by Resilio would have only read and execute permissions for users other than resilio.By setting:
UMASK: 000in the container’s environment variables, Resilio creates files and folders with full permissions (rwx) by default. That ensures the ACL we set up for foo is not overridden by a restrictive file creation mask.
Outcome:
After all these adjustments, new files and folders created or modified by Resilio have ACLs that let both resilio and foo access and modify the data as needed. This configuration allowed my multi-protocol environment - where files can be modified both via SMB (by user foo) and by Resilio Sync - to function without breaking access.
Hope this helps anyone struggling with similar permission challenges!
And please let me know if there is a better solution…!
@patCH, you are the Man! or Woman! Or Being! (whichever one applies ; - ) I look forward to finally getting this up and running, it will save me lots of headaches. Thanks for your hard work!
Interesting. Were you also able to get https working for Resilio Sync’s webGUI?
You’re welcome! I’m glad you found it helpful. I just got upgraded, so I’ve updated the post and added a picture of the ACLs.
For what it’s worth, I had another idea before deciding to stick with the UMASK solution. You could use a Samba Docker image, such as “crazymax/samba,” which allows you to modify the SMB configuration file. This way, you can set the user and group to force, and then mount the share on your machine without overwriting the owner and group when making changes to the share.
I run Traefik on a separate VM and added a service to my Traefik router to proxy the website, allowing me to use HTTPS.
You could also use the “Nginx Proxy Manager” app, which is natively available in TrueNAS Scale.
It works best if you use a public domain along with a free Let’s Encrypt wildcard certificate, such as *.local.yourdomain.com.