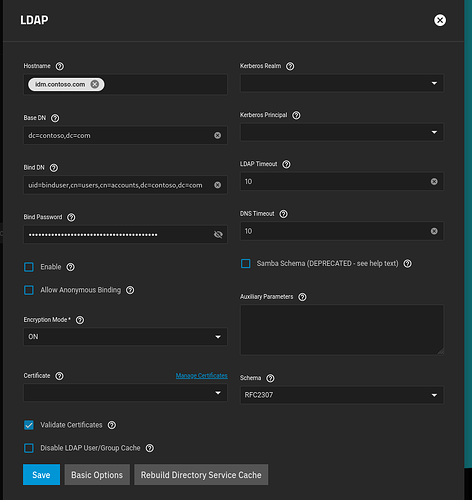
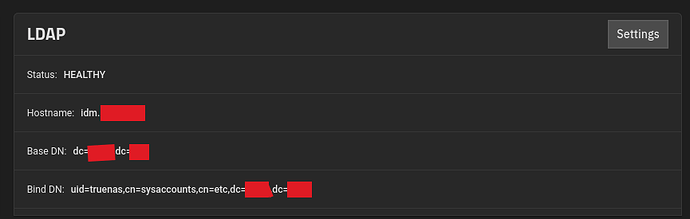
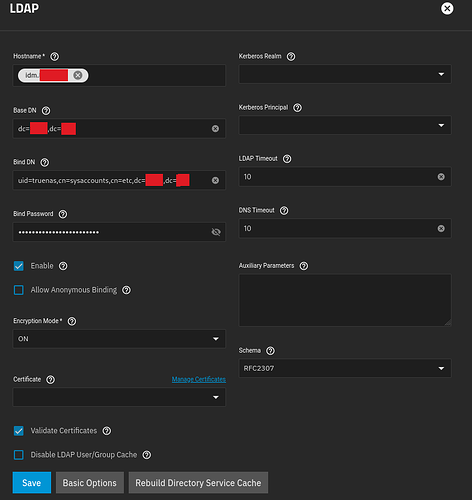
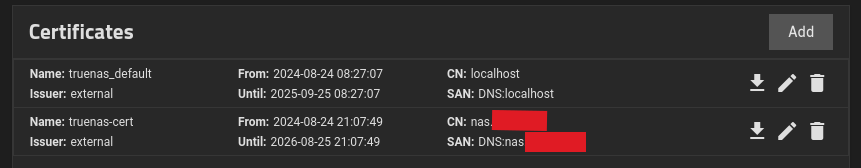
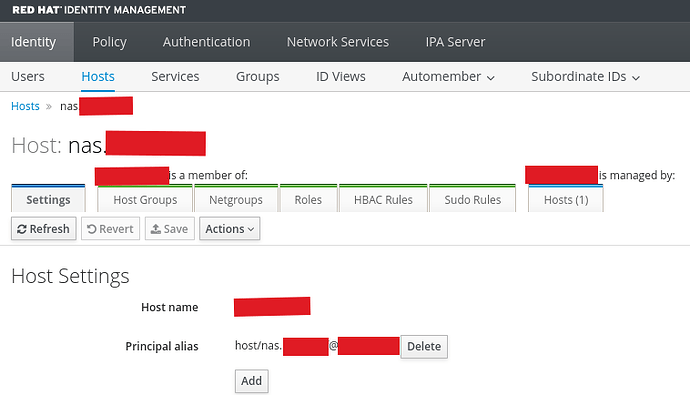
Ok, still having issues. It seems that TrueNAS is looking for permissions to manage its kerberos principal. I’d prefer to not allow that. Is there any way to proceed without granting such permissions?
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/middlewared/plugins/ldap.py", line 912, in __start
dom_join_resp = await job.wrap(await self.middleware.call(
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 692, in wrap
return await subjob.wait(raise_error=True)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 436, in wait
raise self.exc_info[1]
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 488, in run
await self.future
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 535, in __run_body
rv = await self.middleware.run_in_thread(self.method, *args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1364, in run_in_thread
return await self.run_in_executor(io_thread_pool_executor, method, *args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1361, in run_in_executor
return await loop.run_in_executor(pool, functools.partial(method, *args, **kwargs))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3.11/concurrent/futures/thread.py", line 58, in run
result = self.fn(*self.args, **self.kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/utils/directoryservices/krb5.py", line 331, in check_ticket
return fn(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/join.py", line 244, in join_domain
do_join_fn(job, ds_type, domain)
File "/usr/lib/python3/dist-packages/middlewared/utils/directoryservices/krb5.py", line 331, in check_ticket
return fn(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/ipa_join_mixin.py", line 430, in _ipa_join
resp = self._ipa_join_impl(
^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/ipa_join_mixin.py", line 406, in _ipa_join_impl
raise e
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/ipa_join_mixin.py", line 395, in _ipa_join_impl
resp = _parse_ipa_response(join)
^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/directoryservices_/ipa_join_mixin.py", line 39, in _parse_ipa_response
raise CallError(err, extra=err_decoded)
middlewared.service_exception.CallError: [EFAULT] {"result": null, "error": {"code": 2100, "message": "Insufficient access: Insufficient 'write' privilege to the 'krbLastPwdChange' attribute of entry 'fqdn=nas.contoso.com,cn=computers,cn=accounts,dc=contoso,dc=com'.", "data": {"info": "Insufficient 'write' privilege to the 'krbLastPwdChange' attribute of entry 'fqdn=nas.contoso.com,cn=computers,cn=accounts,dc=contoso,dc=com'."}, "name": "ACIError"}, "id": null, "principal": "serviceaccount@contoso.com", "version": "4.11.0"}
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 488, in run
await self.future
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 533, in __run_body
rv = await self.method(*args)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 49, in nf
res = await f(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 179, in nf
return await func(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/ldap.py", line 681, in do_update
await self.__start(job, ds_type)
File "/usr/lib/python3/dist-packages/middlewared/plugins/ldap.py", line 932, in __start
if not err.err_msg.startswith('[KRB5_REALM_UNKNOWN]'):
^^^^^^^^^^^
AttributeError: 'CallError' object has no attribute 'err_msg'