So, with one limitation which will almost certainly go away in Electric Eel since it’s going to docker and that’s what I will use, not vms or jails… Here is my dockerfile to build caddy:
FROM caddy:2.8-builder AS builder
RUN xcaddy build \
--with github.com/caddy-dns/porkbun
FROM caddy:2.8
ENV TZ=America/Chicago
EXPOSE 80 443
COPY --from=builder /usr/bin/caddy /usr/bin/caddy
COPY Caddyfile /etc/caddy/Caddyfile
Here is my caddyfile that is copied in the dockerfile:
{
email redacted
}
import /hosts/*
Here is the hosts file (/hosts directory mapped via hostpath) for the distribution registry:
registry.mydomain.com {
encode zstd gzip
reverse_proxy /v2/* registry-ix-chart.ix-registry.svc.cluster.local:5000
header {
Strict-Transport-Security max-age=31536000;
}
tls {
dns porkbun {
api_key redacted
api_secret_key redacted
}
}
}
If you want to add more hosts with different dns, I’ll have around 15 of them, you simply add each one to the /hosts directory in the container. All your hosts linked to caddy will get their own cert automatically, and renewed, nothing for you to do. The limitation is caddy itself cannot get it’s images from the registry, you’ll have to copy that one manually once and just leave it alone forever as I don’t see any needs for updates to caddy. Well, it can, but, if you ever mess something up with caddy and need a new image (say it isn’t running), you have to manually move one in. So, I just plan to leave it alone other than adding hosts files (that’s the include).
As far as the custom app config, you need hostpaths for:
/data where letsencrypot stuff is stored like your certificates)
/config (caddy config stuff you do not mess with)
/hosts (where you store your reverse proxy config, one per app)
I use a bridge interface for the host interface field, set a static ip and route for 0.0.0.0/0 to my router, change DNS policy to kubernetes first and specify my router as the nameserver and that’s it. This for example checks what’s in my registry:
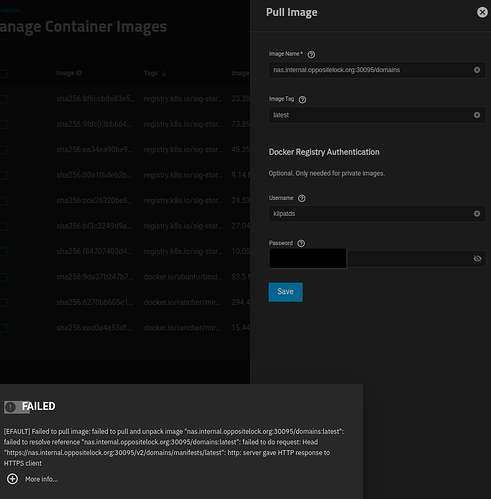
curl -X GET https://registry.mydomain.com/v2/_catalog
DNS for each domain points to caddy static IP. In the “hosts” file for distribution, you see I have a kubernetes DNS name, registry-ix-chart.ix-registry.svc.cluster.local and I obtain that from heavyscript. There’s a kubernetes way to get them, don’t recall off hand as I simply use heavyscript to obtain them all. Note that distribution registry MUST have a port forward else it’s name doesn’t show in internal dns list. None of your reverse proxied apps need static ip, only caddy does and port is irrelevant as caddy translates those.
Hope that helps and finally answers your question.