Hello all,
I want to move my second machine offsite. Currently it’s at least not in the same apartment as my main machine, but I’d like a bit more physical segregation.
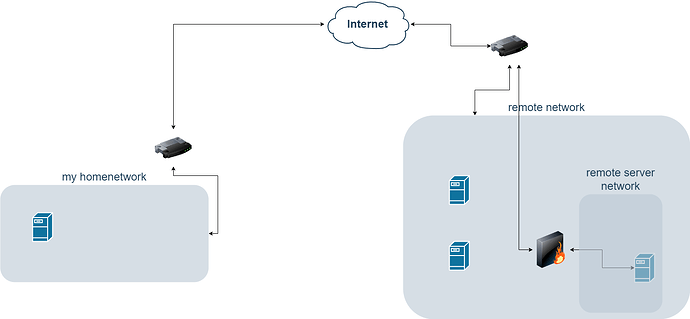
I could place the server at my father in law.
- Access would be via tailscale in order to avoid opening ports on his network
- Segregation of his home network and my server would be the goal
- as far as I know he is not using VLANs nor does he have any kind of advanced network setup going on. It’s just a fritzbox and I assume some generic switches.
- the server should just be a destination for replication tasks / be an available rsync target for another friend
I’m under the impression that truenas assumes on living in a secure network. I have doubts to just move it to some network I’m not the admin of.
- Do I need a physical device that can act as a firewall?
- If so, what cheap device could you recommend (EU / Germany)?
- Is it possible / enough to
disable SSH anduse 2FA on the webgui? - Open to other ideas

If I need additional hardware, low power consumption would be nice.
I was thinking of getting a cheap router for example that would be capable of running pfsense. Connect to the local network on the WAN site and create a LAN that is not accessible from the local network. This way I could hopefully also still connect via IPMI.
Thank you!
Offsite Server
TrueNAS-SCALE-23.10.2
Supermicro X10SLL-F, i3 4130, 16 Gb ECC RAM, Seasonic Prime PX-750
in Fractal Define XL USB 3.0
Data pool: 2x8Tb mirror
Data pool: 1x8Tb stripe
boot pool: 2x128 Gb SSD
UPS: Eaton Eco 650
Main machine staying at home
TrueNAS-SCALE-23.10.1
Supermicro X10SRi-F, Xeon 2640v4, 128 Gb ECC RAM, Seasonic Focus PX-750
in Fractal Design R5
Data pool: 6x4Tb striped mirror + 1 hot spare
VM pool: 2x500Gb SSD mirror
boot pool: 2x250 Gb SSD mirror
UPS: Eaton Eco 1200
NIC: Intel X520 10g