Hello.
I trying to manage self-signed CA / certificates and setup them to be trusted in Firefox/Thunderbird on PC and in iOS devices.
Even I added my self-signed CA to Firefox/Thunderbird/iOS device, the CA signed certificates is still considered as “not trusted”.
Any hints what I doing wrong?
Many thanks in advanced.

Self-signed certificates are generally not trusted by browsers or operating systems because they are not issued by a trusted Certificate Authority (CA). This means the browser cannot verify their authenticity or legitimacy, leading to security warnings and potential user distrust.
1 Like
Is fritz.box an actual real domain or just some imaginary domain for your lan hosts?
I’ll repeat what I said in another thread. Every tinkerer and homelabber should buy a cheap domain, host dns in cloudflare. Makes life so much easier, you can get real Ssl certs free and if you’re lazy, at least a real wildcard cert like *.fritz.box you can use on anything.
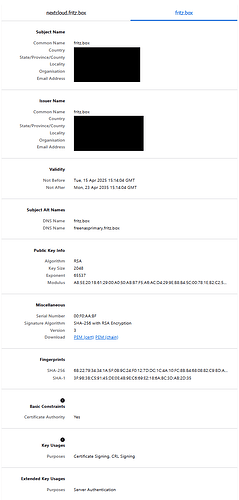
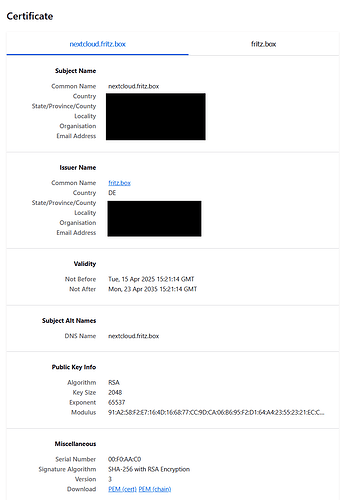
fritz.box is local (i.e. LAN) domain.
It is used by by internet router, which is also local DNS.
All local services use this local domain ‘fritz.box’.
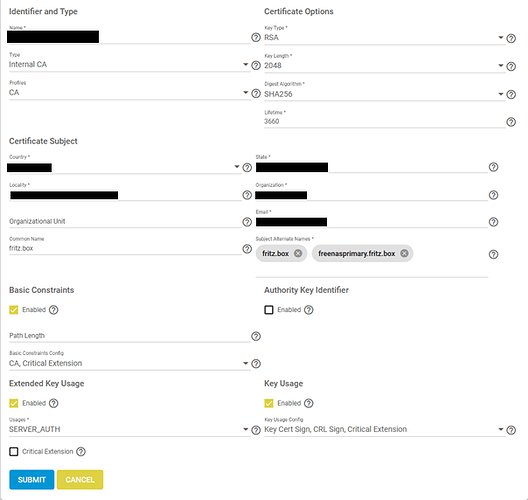
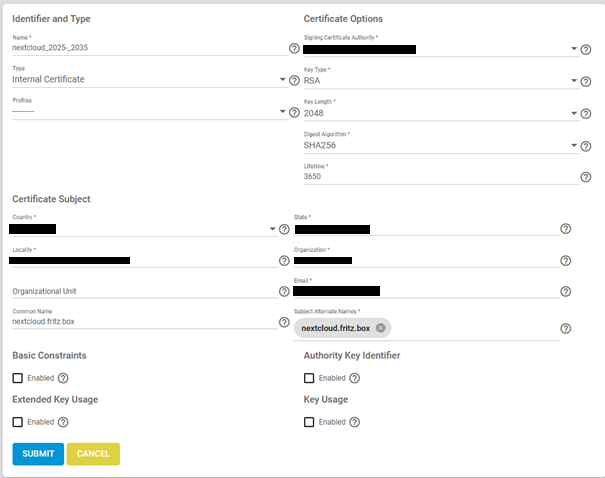
My assumption: when I add my self signed CA certificate for the ‘fritz.box’ domain as trustable into the web-browser, all by this CA signed certificates will be considered as trusted.
But something is still wrong because it just don’t work: I still have to set each certificate as trustable separately.
Do I miss any setting to make it work?
Yeah there’s no real “can I phone home to the internet and check the validity of this cert” because there’s no real certificate authority here. You’d need to create your own CA that is responsible for fritz.box and probably also use certs that export the whole chain (CA, intermediary, host), so then the individual clients looking at the cert phone home to your CA on the lan and give it a thumbs up.
However, in my opinion this is doing it the hard way, just because you want the best of both worlds (a totally custom domain with valid certs). I would spend the ten dollars and buy a domain, and have Cloudflare manage dns for that domain (no it doesn’t really need to manage dns for your hosts, it just needs to give you an API key and deal with Lets encrypt so it can issue real public certs that anyone can validate).
Using Nginx Proxy Manager as a reverse proxy is even better. You can create hostname definitions and tie them to IP/port of your servers, scoot over to the SSL tab, and request and receive a real cert for that server. NPM will then manage that cert and autorenew it when it expires while turning “http:192.168.4.19:8080” into “https://weathervane.fritz.org” or whatever…complete with a real cert.
This is homelabbing, have some fun and experiment.
1 Like