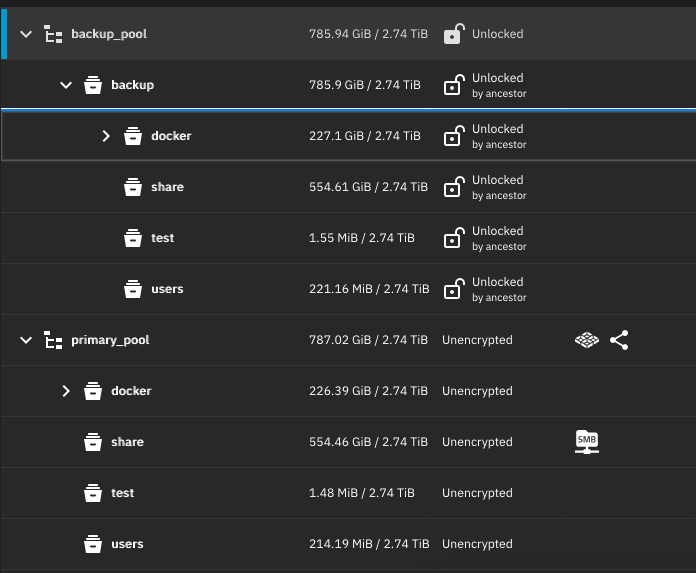
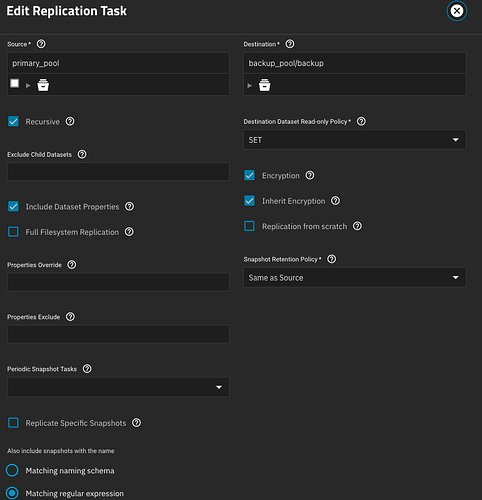
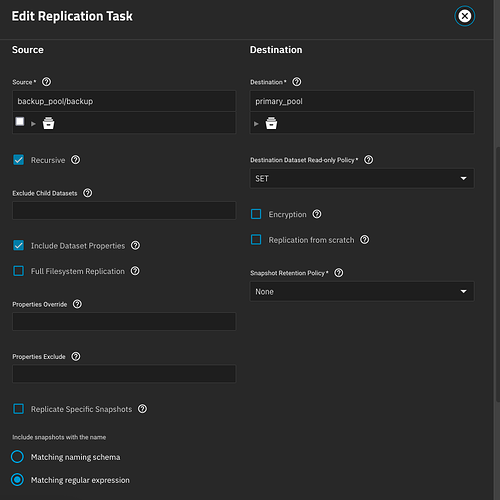
This is what I do, and you can leverage the ability of “raw streams”, which allows you to replicate to a target without the need to unlock either side, and the destination remains in a locked state.
For you to go this route would require starting over, since you cannot just “toggle” encryption on/off for a dataset.
It doesn’t hurt to regularly test and confirm. At minimum, you want to see if you can access the files and even load a few via a readonly dataset with a readonly share, such as photos and videos.
That’s not really the issue. What you were initially describing didn’t really make sense. (Not trying to sound rude.)
If the source dictates the snapshots, which are sent over to the destination, then under normal conditions you should never end up with a destination (backup) that is somehow “newer” than the source.
If you rollback a source dataset to an earlier date, then it’s expected that you will likewise force a rollback on the destination (backup) the next time a replication is sent over. (This is indeed what the recv -F option does. Otherwise, it will abort the replication because “the destination contains modifications that are newer than the source’s latest snapshot”.)
To rollback a source… and then “send back” the latest snapshots from a backup doesn’t make much sense. Why would you even rollback the source in the first place, if you’re just going to reverse “rollforward” again? Maybe for an “accidental” rollback, this could save you. (So can a pool “checkpoint”.)
But intentionally, under normal conditions? I don’t see the reason for doing this.
Because you cannot overwrite an unencrypted dataset with an encrypted replication stream.
By using the “Include Dataset Properties” option, as seen in your screenshot, you are invoking a “raw stream” (-w) under the hood. A raw stream, for an encrypted dataset, sends over the raw, encrypted blocks of data.
Correct. I think you need to look at ZFS snapshots and replications from a different approach. Don’t treat it like SVN or Git, or some file-based version control.