Per request from @Captain_Morgan I’m making this post regarding issue mentioned here: TrueNAS 25.10-RC.1 is Now Available! - #44 by TheJulianJES
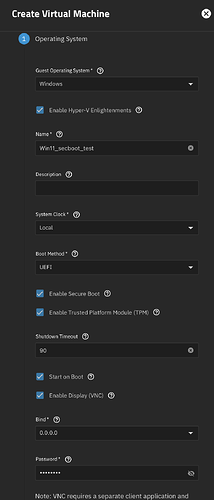
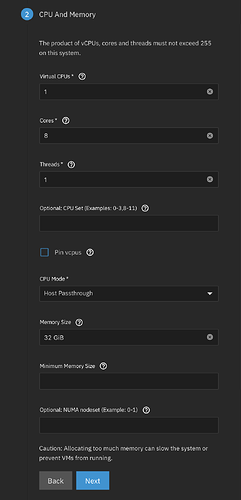
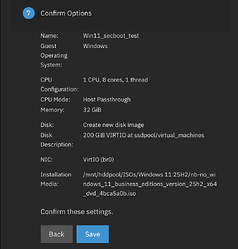
I made one test VM for Windows 11 and one for Debian Trixie. Windows process below:
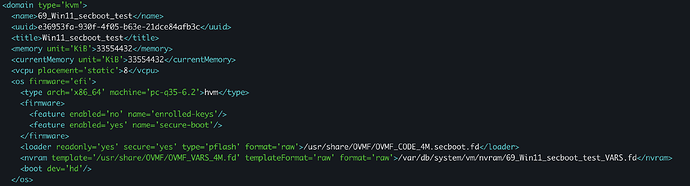
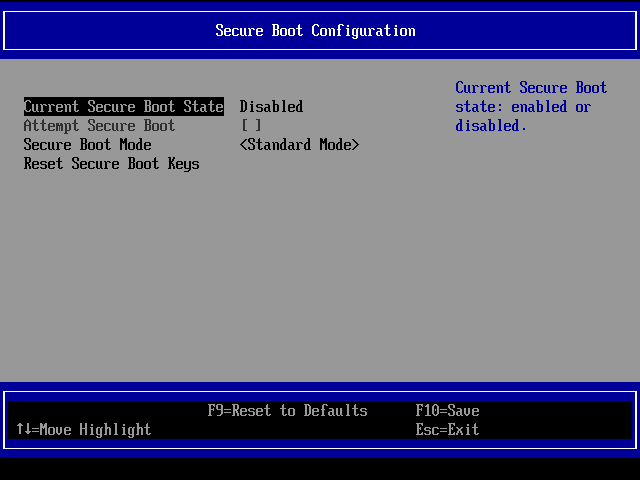
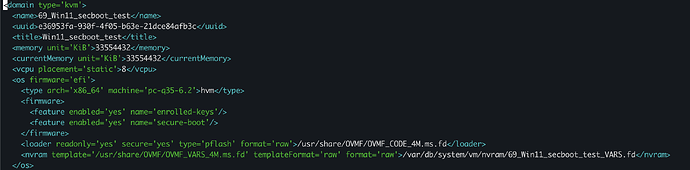
Checking the config with virsh since OS say Secure Boot not enabled:
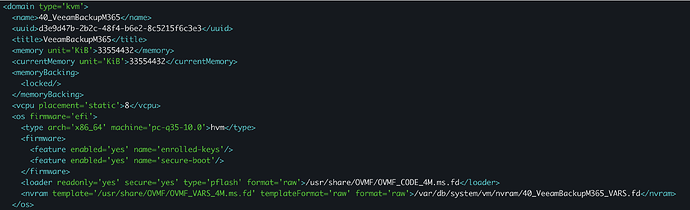
Here we can see that <feature enabled='no' name='enrolled-keys'/> and that /usr/share/OVMF/OVMF_VARS_4M.fd is used as template for VARS.
Trying to set <feature enabled='yes' name='enrolled-keys'/>:
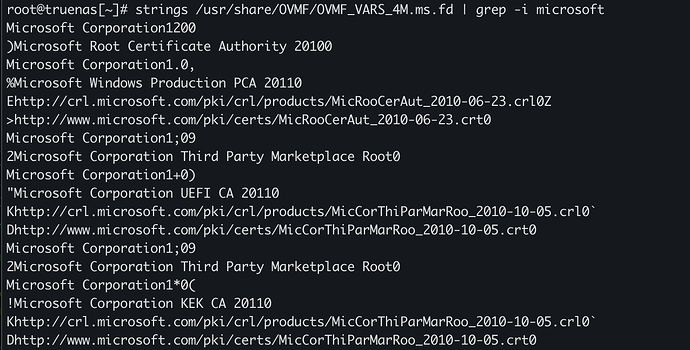
Checking if the VARS file used has Secure Boot keys:
![]()
Nothing.
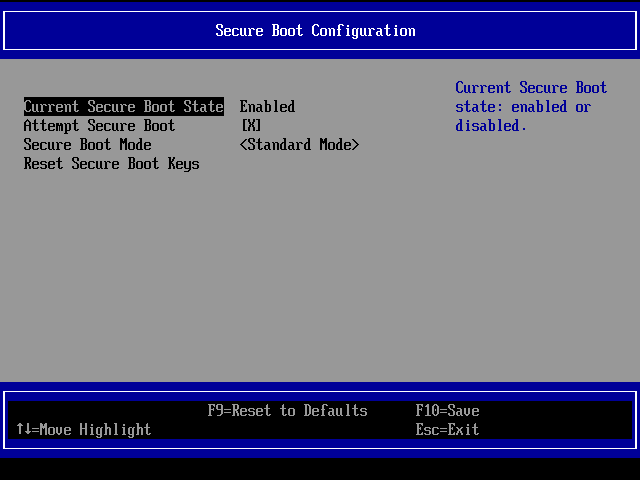
Screenshot from UEFI Setup → Device Manager → Secure Boot Configuration in the non functional VM:
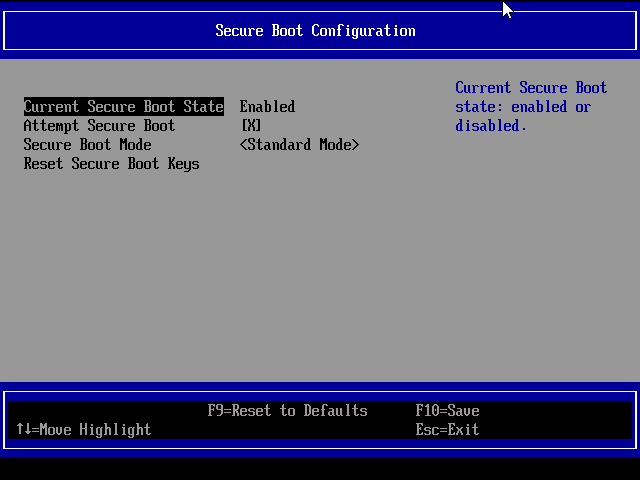
Looking at older pre 25.04 VM that has working Secure Boot with virsh:
It has enrolled keys enabled: <feature enabled='yes' name='enrolled-keys'/>
Checking if the VARS template file used has Secure Boot keys:
Screenshot from UEFI Setup → Device Manager → Secure Boot Configuration in the functional VM:
By the way, the pc-q35-6.2 machine type used as standard i TrueNAS is deprecated in the QEMU version used.