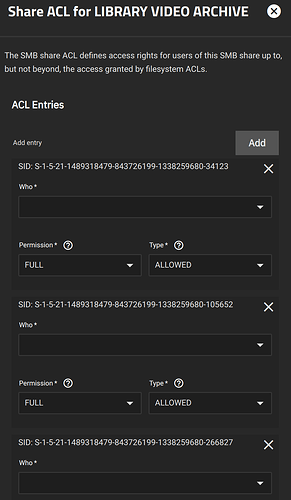
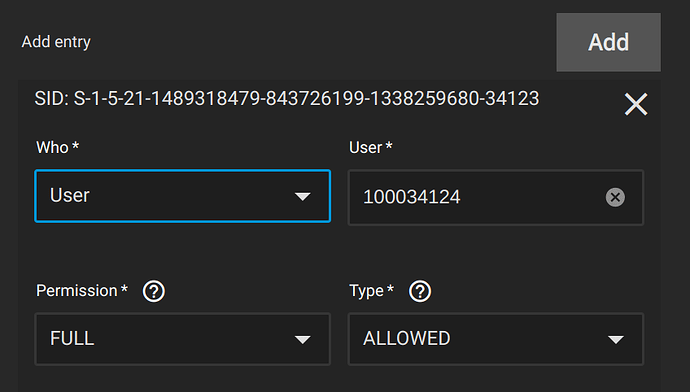
I’ve consistently run into problems with SMB shares authenticating against active directory since installing TrueNAS over a year ago. It was working ok on Cobia and I recently switched trains to Dragonfish on my main NAS and adding users / changing users / doing anything in the GUI that references users is broken. Here’s a screenshot of one of my shares. As you can see the SID populates correctly but it doesn’t know that it’s a user. If I select user, it will figure out the UID and allow it in the user box (but not username) but when saved, it isn’t sticky. Selecting the share acl again looks exactly like the screenshot.
All of the command line tools seem to work correctly. The AD bind is correct (although because of the number of user objects I need to turn off caching as building the cache never succeeds, another thing that is annoying).
Any suggestions? I have to make changes to this share and I currently cannot. And since I can’t just edit a config file the non-functionality of the interface in this regard is causing issues.