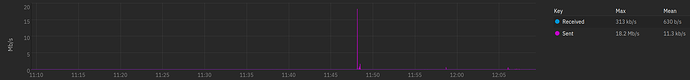
Hello. I’m still new to TrueNAS and really like it so far. I have a new installation of TrueNAS version 25.04.1. I noticed in the dashboard that it looks like TrueNAS is sending data.
I’m wondering what TrueNAS is sending and to where. Can anyone else validate if their TrueNAS systems are doing the same?
You have a web based GUI and you are using it? The system is checking for updates on the web? We can only make wild guesses with such little provided info.
My apologies. That’s the only data I have at the moment. I was wondering if anyone else saw the same and maybe what their system was doing. If you are referencing using TrueNAS using the web base GUI dashboard, that’s where the image I posted came from.
We can not see what you have running on your system. I don’t know if you have VMs, Apps or it is a brand new install with no data.
The system will check for new versions of TrueNAS. It might be NTP for syncing the time and clock. I don’t know if you are playing with the GUI and it is just an update of that.
TrueNAS 25.04.1 is installed on the iron on an NVMe SSD specified for the TrueNAS application itself, no VMs. There are 8 spinning HDDs in this system, 6 TB each. I have several TBs of data copied to this TrueNAS instance at present.
I would suspect the developers, in an attempt to keep TrueNAS updated for versioning and time syncing, would make TrueNAS reach out to do these checks. However, I have no data to suggest that’s what this outgoing data is for.
If you’re using the GUI then the gui populating info for you to view is ‘outgoing data’. This is going to be an annoying answer; download wireshark & do some packet captures.
Good way you can really know what is going back/forth on your network.
1 Like
@Fleshmauler I suspected this is what I might have to do. Thank you.
1 Like
tcpdump command is natively present in TrueNAS Scale - so start with figuring out how much & for how long you want to capture & then you can always send the pcap file to a pc with wireshark installed & then read/investigate from there… unless you love to read raw packet captures over cli