I’m afraid I can’t; this option appears to be undocumented. In fact, the entire process of requesting an ACME cert from a CSR appears to be undocumented. I’d expect it to be on this page:
…since it’s done by clicking the wrench to the right of a CSR:
…but there’s nothing I can see at that page explaining how to actually get the cert.
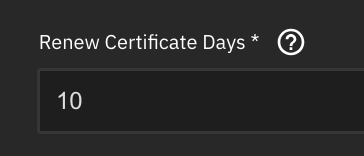
This setting controls when (i.e., how many days before expiration) TrueNAS will attempt to renew the cert. Let’s Encrypt, by far the most popular ACME CA (and the only one TrueNAS supports), recommends renewing at 1/3 life remaining. Since their certs are (by default) valid for 90 days, that means you should begin attempting to renew when 30 days’ validity remain. This is documented in their integration guide, which I linked in the feature request I filed in 2022.
No idea; the UI doesn’t say. It lets me enter 99 without complaint though.
I don’t know what the max is, or even if there is one, so I can’t say whether it’s too low (though I doubt it), but the default definitely is.
There were at least two, three years ago, linked up-thread (and a third, also linked up-thread, that would have been more in-line with OP’s request, but admittedly would have been a bigger change to the code). Nothing was done with them. When you ignore objectively-obvious fixes that would take about one line of code, it doesn’t exactly motivate us to start over in the new system.
This is encouraging, I guess–better late than never and all that. There are really only two pieces of information the system should need in order to obtain a cert from Let’s Encrypt:
- Which FQDN(s) are on the cert, and
- How will Let’s Encrypt validate domain control?
- i.e., which DNS host, with which credentials?
There’s absolutely no reason to create a CSR first. There’s even less reason to require information be included in that CSR that’s just going to be discarded by the CA anyway–country, state, org, locality, and email will be ignored by the CA and stripped from the issued cert (because Let’s Encrypt can’t validate any of them). There’s no reason, really, to even have the cert options–I guess expose RSA vs. ECC and key length, but the rest is all needless complication. And even that can probably be hidden behind an “advanced settings” button.