Could you tell me which part of my guide you’re referring to here? I would love to update the guide to be more clear if I knew.
@ owl
Wow, just wow. Thanks for putting all this together and in such a thorough manner. Am also really glad to see you getting it working.
Unfortunately, it’s still not working on my end. Given the router provided DDNS in the format of subdomain.domain.tld, I’ve tried both *.domain.tld and *.subdomain.domain.tld in the Subject Alternative Name fields.
In both cases, I’ve get a 502 Bad Gateway, which seems to suggest NPM is not forwarding the traffic across to [FileBrowser/NextCloud] (?)
Not sure if this information is useful.
@ owl
I was actually referring to the Techworks guide above and at any rate looks like you’ve already picked up on it as above.
It’s worth noting that I myself have been using a free subdomain from Dynu for every part of this guide, and it sounds like you are in the same position as me (i.e., you have access to a subdomain but not the domain that it falls under).
As far as the scope of what you are trying to do is concerned, subdomains should function the same as domains, but it is important to remember that, if you are using a subdomain, you must replace all references to mydomain.tld in my guide with your subdomain (i.e., mysubdomain.domain.tld). This means that:
- Your Nextcloud host, OVERWRITECLIURL environment variable and Domain Name in Nginx Proxy Manager should all be something like nextcloud.mysubdomain.domain.tld.
- Your Collabora Server Name should be something like collabora.mysubdomain.domain.tld:443 and your Collabora Domain Name in Nginx Proxy Manager should be something like collabora.mysubdomain.domain.tld
- The Subject Alternative Name for your self-signed SSL certificate should be *.mysubdomain.domain.tld and not *.domain.tld.
Also, you mentioned that you are using the DDNS that is provided by your router, but you still have an online account with whichever DDNS service you are using, right? I’m just asking this because it might also be worth logging into your DDNS account and examining things like the DNS records to make sure there’s nothing fishy going on there.
Forgive me if you have already done all of this. I’m just trying to exhaust the obvious solutions first. The cause of a 502 Bad Gateway error can often just be one of the aforementioned things being set incorectly.
I see, good to keep in mind.
Thanks! But also, I don’t think I could have gotten it working without your input. I appreciate you keeping me in the loop. I am learning a lot, too.
@ owl
Yep that’s right
Yes that’s my understanding and what I’ve done also. (Just for completeness, I’m currently using FileBrowser instead of NextCloud now, and not using Collabora. That said, that’s hopefully not relevant as the issue seems to be about NPM).
The DDNS provided by my router acts like a function / value added service it seems. ie. Within the router interface, you switch on/off the function, select a DNS Service Provider and (sub)domain name) and it’s all set. There isn’t much scope for anything else to be checked, though that said, what else can I check?
No, thanks for giving it as much thought as you have.
Just to state my understanding explicitly in case I got something wrong:
- external traffic on port 443 is directed to NPM via port forwarding on the router;
- NPM then forwards the port 443 traffic to the internal ip (device) running the service (FileBrowser in this case)
The 502 Bad Gateway seems to be implying the traffic is indeed being forwarded to NPM, but NPM is forwarding it to the wrong place? (Otherwise the error would be about an unresolved domain name or similiar)
A question that comes to mind as I write this is how does NPM know what traffic received from which external port to forward to which internal port? eg. If I port forward on my router ports 100 and 101 to my NPM instance, in NPM we only set the destination address in the Proxy Host settings. There’s no setting that determines the destination address should receive traffic from which external port?
@ owl
jfc it finally worked
The 502 Bad Gateway errors did indeed suggest a traffic forwarding problem with NPM.
Changing to the Forward Hostname / IP to local IP running the FileBrowser instance from ```localhost`` was the critical change. Completely idiosyncratic but I’m going to take what I can get.
Conversely playing around with the SSL certificate settings didn’t have any impact for me (ie. wildcard settings on domain name, Common Name & Subject Alternate Name)
This has been a highlight for me poking around with networking, etc. Thank you again.
Some cleanup points for anyone else who might find this useful:
Back to a fundamental understanding of how network traffic works:
- access to a service (eg. FileBrowser/NextCloud/etc) as provided by a server is done by entering a domain name
- the domain name is converted to an IP, in particular an external IP if accessing externally
- receipt and transmission of traffic from the external network (WLAN/internet) to internal network is handled by the router
As such, what determines what traffic the Proxy Host should be forwarding to which destination address is the Domain Name input in NPM (and has nothing to do with ports).
This was enlightening for me at least.
Thank you so much, I was trying to run the built-in CODE server with no luck…this saved me.
Hi Everyone,
I am having a similar issue with nextcloud and could use some help.
I am using RC2 of electric eel.
I had next cloud running at one point, but it failed and would not redeploy. I deleted the container and tried to recreate it. Now it wong create at all. I checked the /var/log/applifecycle file and found the following.
[2024/10/11 11:55:48] (ERROR) app_lifecycle.compose_action():56 - Failed ‘up’ action for ‘cloud’ app: Network ix-cloud_default Creating
Network ix-cloud_default Created
Volume “ix-cloud_tmp” Creating
Volume “ix-cloud_tmp” Created
Volume “ix-cloud_bitnami_redis_data” Creating
Volume “ix-cloud_bitnami_redis_data” Created
Container ix-cloud-permissions-1 Creating
Container ix-cloud-permissions-1 Created
Container ix-cloud-redis-1 Creating
Container ix-cloud-postgres-1 Creating
Container ix-cloud-postgres-1 Created
Container ix-cloud-redis-1 Created
Container ix-cloud-nextcloud-1 Creating
time=“2024-10-11T11:55:41-06:00” level=warning msg=“config uid, gid and mode are not supported, they will be ignored”
time=“2024-10-11T11:55:41-06:00” level=warning msg=“config uid, gid and mode are not supported, they will be ignored”
Container ix-cloud-nextcloud-1 Created
Container ix-cloud-nginx-1 Creating
Container ix-cloud-cron-1 Creating
time=“2024-10-11T11:55:41-06:00” level=warning msg=“config uid, gid and mode are not supported, they will be ignored”
time=“2024-10-11T11:55:41-06:00” level=warning msg=“config uid, gid and mode are not supported, they will be ignored”
Container ix-cloud-nginx-1 Created
Container ix-cloud-cron-1 Created
Container ix-cloud-permissions-1 Starting
Container ix-cloud-permissions-1 Started
Container ix-cloud-permissions-1 Waiting
Container ix-cloud-permissions-1 Waiting
Container ix-cloud-permissions-1 Exited
Container ix-cloud-redis-1 Starting
Container ix-cloud-permissions-1 Exited
Container ix-cloud-postgres-1 Starting
Container ix-cloud-postgres-1 Started
Container ix-cloud-redis-1 Started
Container ix-cloud-postgres-1 Waiting
Container ix-cloud-redis-1 Waiting
Container ix-cloud-permissions-1 Waiting
Container ix-cloud-permissions-1 Exited
Container ix-cloud-postgres-1 Error
Container ix-cloud-redis-1 Healthy
dependency failed to start: container ix-cloud-postgres-1 is unhealthy
How do I fix this? I have already created 3 new data sets for app data, user data, and database. app data and user data have www-data owner and group permissions.
@owl
Thank you very much for this detailed guide, I have to say one of the best out there.
Would this setup also work with a router which only supports IPv6?
@owl You sir are a genius! I have spent six hours over three days troubleshooting trying to get nextcloud, collabora, and nginx truenas scale apps to play nice together. I have read through MANY of guides but none of them applied to my setup until i ran across yours. Thanks for taking the time to help the community.
That’s awesome! I’m so glad you figured it out. I just tested this out myself and confirmed that I was not able to access my Nextcloud installation when I changed the Forward Hostname / IP for my Nextcloud proxy host in Nginx Proxy Manager to localhost.
So I guess what you’re saying is that, by the time external traffic gets to Nginx Proxy Manager, it has already been transmitted down a port (normally either port 443 or port 80) which was determined by the router, and so Nginx Proxy Manager does not need to worry about knowing which external port it should be listening to, like you were asking about here:
For a while, I only had port 443 open on my router. Then, I also opened port 80, but I don’t think that it was necessary to do this. All traffic to my network seemed to be going through port 443 anyway. I think port 443 is just the default these days for URLs, especially when connecting via https.
Still, it makes me wonder how one would force incoming connections to be served through port 80.
No problem!
Thanks!
I have been messing around with this for the past few hours and I haven’t been able to find a way to connect to Nextcloud over IPv6. Granted, I don’t have much experience with IPv6, but I think the idea behind IPv6 is that you can bypass port forwarding entirely as long as you have configured your network to allow incoming IPv6 connections.
If there is a way to connect to Nextcloud externally using IPv6, I am not sure whether it would involve going through Nginx Proxy Manager first or just connecting directly to the Nextcloud server (which, presumably, would require getting a unique IPv6 address for your Nextcloud server, which was something I wasn’t able to figure out how to do).
As per this post, it would appear that IPv6 is not officially supported for TrueNAS SCALE apps quite yet.
Tentatively yes (and happy to be corrected by anyone more knowledgeable). As a rough understanding, the key protocol required (which I guess is in line with browser access) is TCP and UDP. So with NPM installed, it’s basically handling all TCP and UDP protocol via http (port 80) and https (port 443). Specifically who/what device to forward the traffic from there is determined by the destination IP and port specified in the NPM proxy settings.
If you just forward traffic on port 80 to the device running NPM (ie. external port 80 to NPM device on (default) port 30021), it’ll do it as well as it did for port 443 (ie. external port 443 to NPM device on (default) port 30022)? You know you’ve done it correctly if you get the NPM ‘Congratulations’ page.
Thank you so much for this guide. I was pulling my hair out trying to change the config.php to no avail. Followed your guide and everything seems to be working (NC and NPM), fingers crossed that the collabra part works.
I wonder if one could use the occ tool to set OVERWRITEHOST and OVERWRITECLIURL after the install?
Hi @owl
Thank you very much for testing, really appreciate it.
I made the radical decision to switch the internet provider and now everything works as expected!
I ran into another problem when uploading big files (<4GB).
According to Upload big files I have to manipulate
php_value upload_max_filesize 16G
php_value post_max_size 16G
but I can’t seem to find where I need to do this.
Do you know where I can override these values?
How I got mine to work with Nextcloud running on TrueNAS using a Rpi 3 my DNS provider & Nginx Proxy.
Cloudflare
- Create an
Arecord pointing domain to private address of your Nginx Proxy Manager:npm.example.com - Create a
CNAMErecord for all subdomains:*.example.com
Pi-hole (Docker Tag 2024.07.0 Pi-hole v5.18.3 FTL v5.25.2 Web Interface v5.21) configuration
- Add DNS record pointing to the Nginx Proxy Manager host:
npm.example.com -> 192.168.x.x - Add a CNAME record:
nc.example.com -> npm.example.com
TrueNAS (ElectricEel-24.10.0.2) Config
- clear the
Hostname field - Use the
truenas_defaultcertificate - No additional environment variables
- Uncheck
Use different port for URL rewrites - Port
9001
Nginx Proxy Manager (v2.12.1)
- Proxy Host entry:
- Domain Names:
nc.example.com - Scheme:
https - Forward Hostname / IP:
Truenas' private ip on my network - Port:
9001 - Custom Nginx Config:
client_body_buffer_size 512k; proxy_read_timeout 86400s; client_max_body_size 0;
- Domain Names:
- SSL Certificate creation:
- Can’t include links here but I created an API token for my cloudflare domain so I could use Cloudflare for the DNS challenge
Nextcloud config.php modifications
'overwrite.cli.url' => 'https://nc.example.com''overwritehost' => 'nc.example.com''overwriteprotocol' => 'https'- Add
nc.example.comtotrusted_domains - Add Pihole’s ip address to
trusted_proxies - I’d also back this file up as I don’t know what will happen to it during an update through TrueNAS
Is it possible to access nextcloud remotely through a custom location on a proxy host? For example, I would like to access my nextcloud with mydomain.com/nextcloud.
I have a proxy host set up like this:
- Source:
mydomain.com - Destination
https://server.ip:444(444 is where my truenas scale gui is set to) - port forward 433 to 443 which is where my nginx proxy is listening on
- so when I go to
mydomain.comit sends me to the truenas scale login screen.
custom location:
- define location: /nextcloud
- scheme: https
- forward hostname / IP: server.ip
- forward port: 30027
I am still trying to get to get other parts working as I have had troubles with my first login and now troubles reinstalling nextcloud. But this is the error I get for this part.
“Nextcloud Page not found. The page could not be found on the server or you may not be allowed to view it. Back to Nextcloud Nextcloud – a safe home for all your data”
Do I have to reinstall every time I make changes to the host or install wizard settings? I had checked the config.php file and it did not look like some settings were being saved (like host).
ElectricEel-24.10.0.2
This is an amazing write up I was at my wits end trying to make this work. Thank you so much for posting this. Truly this should not be this much tinkering to get this to work but here we all are lol. NextCloud and TrueNAS please get this process to be smoother. it does not have to be perfect but way too much digging to install this product. Thanks again
Thank you so much for this amazing resource !
I actually had nextcloud + collabora setup but decided to do DNS with cloudflare so I could scale up the service to my family.
now ofc it isnt working with the new domain.
I have an issue that my collabora domain doesnt work when putting it in the server url - i get an error:
“Could not establish connection to the Collabora Online server.
Failed to connect to the remote server: cURL error 28: Connection time out after 5001 milliseconds …”
although https://cods.domain.com/hosting/discovery shows the xml with the correct domain and scheme.
when putting my truenas ip instead with port 9980 I am able to connect and see the correct url’s, but trying to load documents shows:
“Document loading failed Failed to load Nextcloud office - please try again later”
i’ve tried to troubleshoot this issue for days now…
I have tailscail + nginx + nextcloud + collabora as described above, on truenas Electric Eel.
did everything in the guide to the word, first with both certificates, than both without certificates, than colabora with and nc without.
for every attempt i get:
“Document loading failed Failed to load Nextcloud office - please try again later”
Hi @owl
I have recently installed my TrueNAS server and this is my first one, so I’m new. I’ve checked a lot of websites and a lot of forum entries. Yours was quite helpful and tried more options from here but still without success.
My setup:
Truenas Scale: ElectricEel-24.10.2.1
Tp-link router - no port forwarding setup
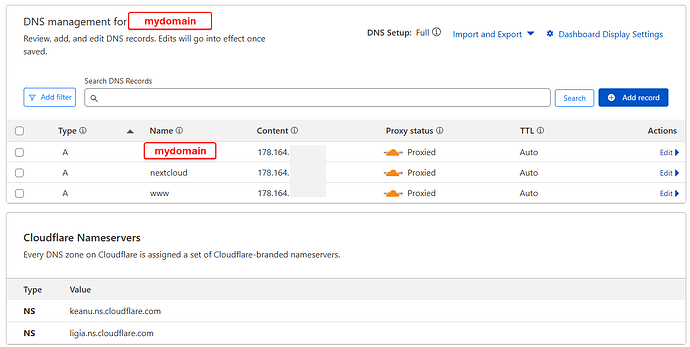
Domain from a registrar but managed on Cludflare:
DNSSec not enabled
Mydomain is using automatic SSL/TLS. Encryption mode is set to Cloudflare’s recommendation.
I have created a Cloudflare tunnel to TrueNAS - status healty
Public hostname: (NO subdomain) - mydomain
Service: HTTPS://192.168.x.x:30022 - Ngnix port for 443 (tried also with Nextcloud port: 30027)
Cloudflared is running on TrueNAS
Nginx Proxy Manager (App Version: 2.12.3; Version: 1.1.14)
My Ngnix Proxy Manager settings are the followings:
Proxy host:
- domain names: *.mydomain, mydomain, nextcloud.mydomain
- scheme: https; server ip; 30027 (nextcloud port)
- only block common exploits is turned on
- SSL certificate: *.mydomain, mydomain
- all the settings turned on: force SSL, HTTP/2 support, HSTS enabled, HSTS subdomains (experimented with setting these off - no luck)
- Stauts is Online, access: public
SSL certificate: - Let’s Encrypt certificate is setup with Cloudflare token (DNS challenge) with the domain names: *.mydomain, mydomain and the certificate’s status shows “in use”.
Nextcloud (App Version: 31.0.2; Version: 1.6.18)
Nextcloud has been installed with the following settings:
- Host left blank
- Additional environment variable: OVERWRITEHOST - value: nextcloud.mydomain
- Certificate ID: ‘truenas_default’ certificate ; Use diffferent port for URL rewrites (checked) → port: 443
- Nextcloud config.php
Automaticly set (no change): ‘overwrite.cli.url’ => ‘https://nextcloud.mydomain’
Automaticly set (no change): ‘overwritehost’ => ‘nextcloud.mydomain’
Automaticly set (no change): ‘overwriteprotocol’ => ‘https’
trusted_domains already contained nextcloud.mydomain
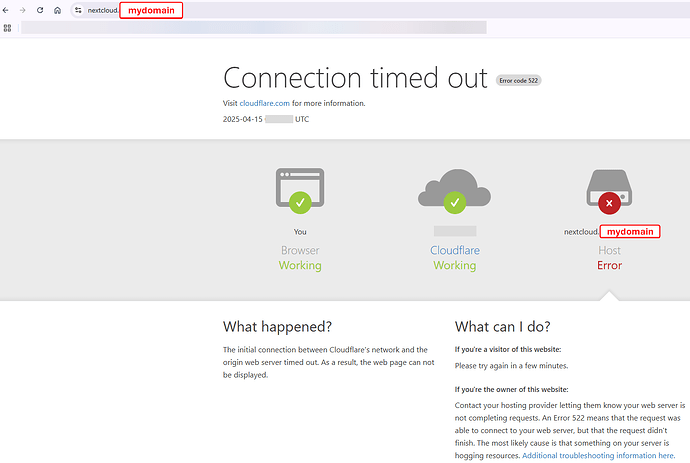
When I don’t set the hostname, then Nextcloud is available from LAN but not from the internet.
Generally I receive the following error, at least when tried with https then it does not display “insecure connection”:
Please help me further, I’m stuck.
Any help is appreciated.
Thank you.