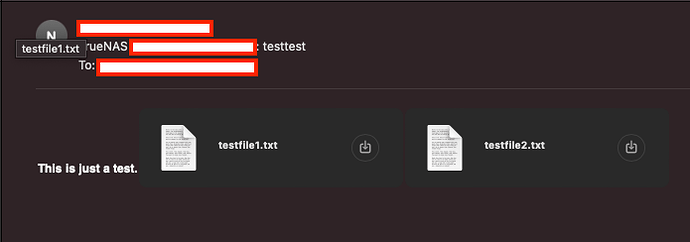
SOLUTION IS HERE:
First I really need to thank everyone who helped out here, I would have been lost for weeks without that help. We have a very good community.
I am presenting two functions, one to send the email, one to generate the attachments.
The first is the send_email function. Consider the variables as global, in my script I really do not have this as a function, it is for simplicity.
Variables are: $subject, $html_data, and $email
If the file /tmp/attachment.json does not exists then we send email without an attachment.
If the file /tmp/attachment.json does exist, then we use curl to send the attachment(s).
send_email() {
if ! test -e "/tmp/attachment.json"; then
midclt call -job mail.send '{"subject": "'"${subject}"'", "html": "'"${html_data}"'", "to": ["'"${email}"'"]}'
else
curl -k –location-trusted -v -u truenas_admin:santa -F 'data={"method": "mail.send", "params": [{"subject": "'"${subject}"'", "to": ["'"${email}"'"], "html": "'"${html_data}"'", "attachments": true}]}' -F "file=@/tmp/attachment.json" http://127.0.0.1/_upload/
rm /tmp/attachment.json # Cleanup
fi
}
The second is create_attachment function and it will create the attachment.json file.
We call the function like this:
create_attachment_file /mnt/farm/scripts/report_body.txt report.txt
Where the first parameter is the full path and name of the file to be sent.
Where the second parameter is the name of the file as presented in the email.
In the example above we are sending the file /mnt/farm/scripts/report_body_.txt and in the email it will be named report.txt.
If you have multiple files to send, run the create_attachment_file function for each file you want attached, then once you have all your attachments in place, run the send_email function.
create_attachment_file() {
encoded_content=$(base64 --wrap=0 $1)
if test -e "/tmp/attachment.json"; then # If the file exists then we need to add on to the end, but need to delete the last ']'.
# I need to read the file back, remove the last 2 lines, add line ' },', then add new header.
updating_attachment=$(head -n -2 /tmp/attachment.json) # This removes the last lines.
(
echo "${updating_attachment}"
echo ' },'
echo ' {'
echo ' "headers": ['
echo ' {'
echo ' "name": "Content-Transfer-Encoding",'
echo ' "value": "base64"'
echo ' },'
echo ' {'
echo ' "name": "Content-Type",'
echo ' "value": "application/octet-stream",'
echo ' "params": {'
echo ' "name": "'"$2"'"'
echo ' }'
echo ' }'
echo ' ],'
echo ' "content": "'"$encoded_content"'"'
echo ' }'
echo ']'
) > /tmp/attachment.json
else # Else we generate the initial file.
(
echo '['
echo ' {'
echo ' "headers": ['
echo ' {'
echo ' "name": "Content-Transfer-Encoding",'
echo ' "value": "base64"'
echo ' },'
echo ' {'
echo ' "name": "Content-Type",'
echo ' "value": "application/octet-stream",'
echo ' "params": {'
echo ' "name": "'"$2"'"'
echo ' }'
echo ' }'
echo ' ],'
echo ' "content": "'"$encoded_content"'"'
echo ' }'
echo ']'
) > /tmp/attachment.json
fi
}
Another piece of advice, while this does run in TrueNAS 24.10.0.2 and 24.10.1, it will not run in CORE so you will need to resort back to sendmail. I test the version of TrueNAS, anything less-than 24.x will use sendmail, anything equal or greater will use the new mail sending commands. I need to figure out how to implement this without changing a lot of HTML code. I think it will be a lot of if statements.
I would like to say that I have not incorporated the $html_data into my script however the static values I provided worked fine.
Hope this helps everyone, it has certainly helped me.