This is similar to the guide that idevpy made, however I ended up having issues with using Radarr/Sonarr to automatically import files correctly and download permission issues. So posting the the YAMLs I ended up using that worked well.
TrueNas Scales App Side:
Install Dockge
Give it access to the following datasets:
Gluetun Config Dataset
qBittorrent Config Dataset
Torrent Download Dataset
Resources: Give it enough resources to run the VPN and qBit, I’m running it with 4vCPUs and 10GB RAM, can probably just leave these on defaults to be honest.
Dockge Side
Gluetun (VPN):
Click “Compose”
Call it “gluetun” or similar
version: "3"
services:
gluetun:
image: qmcgaw/gluetun
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8888:8888/tcp # HTTP proxy
- 8388:8388/tcp # Shadowsocks
- 8388:8388/udp # Shadowsocks
- 8080:8080 #qbittorrent
- 6881:6881 #qbittorrent
- 6881:6881/udp #qbittorrent
volumes:
- /mnt/AppPool/Apps/gluetun - #CHANGE TO CONFIG FOLDER
environment:
# See https://github.com/qdm12/gluetun-wiki/tree/main/setup#setup
- VPN_TYPE=openvpn
- VPN_SERVICE_PROVIDER=private internet access
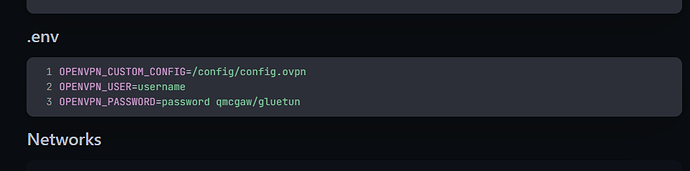
- OPENVPN_USER=USERNAME
- OPENVPN_PASSWORD=PASSWORD
- SERVER_REGIONS=UK London
networks:
10.0.100.0/24: {} - #CHANGE TO LOCAL CIDR IF REQUIRED so VPN doesn't break if calling local resources
Follow instructions for your chosen VPN, I used PIA, so I left the config I used for UK London server for that - gluetun-wiki/setup/providers at main · qdm12/gluetun-wiki · GitHub
qBittorrent
services:
qbittorrent:
image: lscr.io/linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=0 - #CHANGE THIS IF YOU DON'T WANT TO RUN AS ROOT
- PGID=0
- TZ=GMT+1
- WEBUI_PORT=8080
- TORRENTING_PORT=6881
volumes:
- /mnt/AppPool/Apps/qbitconfig:/config #qbit config location
- /mnt/DataPool/Media/Torrents:/mnt/DataPool/Media/Torrents #where you're downloading to
restart: unless-stopped
network_mode: container:gluetun
networks:
10.0.50.0/24: {} #CHANGE to local CIDR if required
For the volumes, you need to follow the following format:
For Config:
/mnt/path/to/config:/config (make sure that :/config is there)
For download location you need to put the path, then the : then the path again, otherwise Sonarr/Radarr doesn’t recognise the path and can’t import correctly.
/mnt/Path/to/Downloads:/mnt/Path/to/Downloads
qBittorrent note:
Remember that qBittorrent uses a random password to begin with when you compose it for the first time, the password will be in the terminal log of the docker image within Dockge.
Log into qBit, go to Tools > Options > WebUI - then change the password. This will reset each restart otherwise.
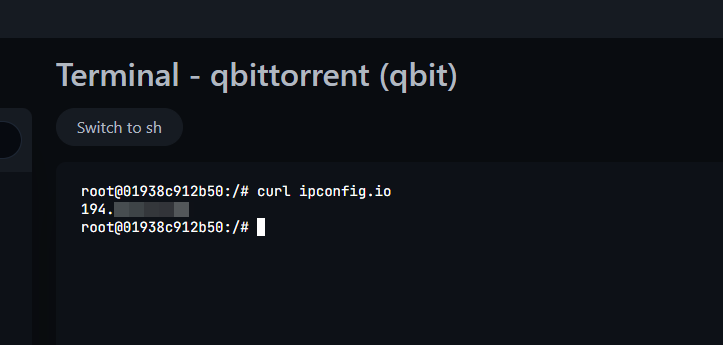
You can test that the VPN is working by clicking “bash” on the container and typing in “curl ipconfig.io”, it should return a public IP from the VPN provider.
Like so:
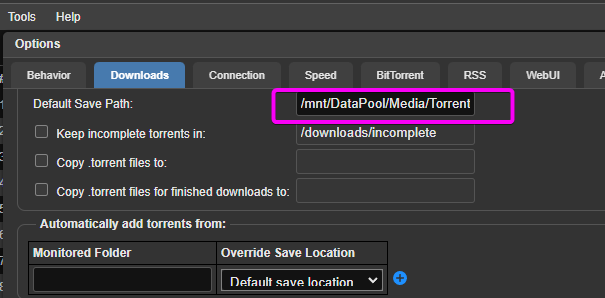
The qBit Download Location should automatically fill with your path, if it doesn’t, swap it to the correct path:
Config from Sonarr/Radarr side is all exactly the same as you’d expect, I didn’t need to change anything there.
Hope this helps ![]()