Hello! I am new in this topic.
What I would like to achieve: I have installed Nextcloud on TrueNAS for media and file share for home use (not enterprise) and have setup a dynamic DNS and port forwarding for Nextcloud on the router to reach it from the internet.
Everything works good on http but when I turn on “HTTP to HTTPS redirect” in TrueNAS then Nextcloud still reports “Accessing site is insecure via HTTP…”. Then I browsed a lot of websites and installed Nginx Proxy Manager and setup proxy host with Nextcloud port 30027 with a Let’s Encrypt certificate, set the scheme to https and then Ngnix showed the certificate is online. Now when I try to open mydomain.org:30027 the browsers display the connection isn’t private and when I choose continue to the site (unsafe), then the error says it took too long to respond. When I turn on “HTTP to HTTPS redirect” on TrueNAS then some settings get wrong - I had to reinstall Nextcloud couple of times.
What I would like to achieve is an https connection for Nextcloud and TrueNAS. When also possible, then setup using mydomain.org instead of mydomain.org:30027
Is it possible to setup e.g. a VPN connection for administering the server remotely or is it not recommended? Would the whole setup secure enough or should I still do additional security measures?
Basically I want to reach the server from the internet securely (if VPN client install is not needed on each client) and share files/photos with friends over Nextcloud also securely.
I have not much expertise on setting up these things, so please give me some guidance what to do.
Thank you in advance.
GM
I have one question, who (all) will be using it remotely?
If it’s just you or your household, then, use Tailscale. It will allow you to seamlessly access your data at home whereever it is. Even better is if your router supports Tailscale. Mine does, an ASUS using Merlin firmware.
Tailscale will connect the VPN for you when not at home, and unconnect when at home. Seamless. No security issues. Personally, I would never expose Nextcloud to the internet but that’s me.
I have a Tplink router and it supports OpenVPN and PPTP VPN.
The system is for family use. The remote access would be when travelling, not at home, then also reach our data and stream our music (e.g. Emby, Jellyfin) and backup our cell phones through Nextcloud, etc.
I chose Nextcloud because their platform seemed a comprehensive private cloud solution.
I would share photos / videos with friends and other family members not living with us.
Any advise is welcome.
I expose my Nextcloud using Cloudflare tunnels. Inside my home network, NGINX handles the proxy and the certificates. Outside of my home network, Cloudflare handles the certificates. I also appreciate not having to port forward or punch holes in my firewall. The Cloudflare tunnel daemon is smart too. Inside my home network it is one hop to get to my Nextcloud server. Traffic does not go out to the internet and back. I use Tailscale to do administrative tasks and server management when I am not home. My homelab is accessible via Tailscale installed on my pfSense router. But you could easily use something like Tailscale for all your Nextcloud users.
Your suggestions are very good.
Maybe I did something wrong, please correct me.
I’ve turned off port forwarding on my router.
I have setup a Cloudflare tunnel based on Create a Cloudflare Tunnel · Cloudflare Learning Paths
The public hostname for the domain: mydomain (path is blank), service: http://192.168.0.111:30027 (this is for Nextcloud).
Ngnix setup:
Proxy host: mydomain; http://192.168.0.111 (should I put a * in front of the domain name?), forward port: 30027.
Cloudflare asks me to change the name servers for their nameservers. Though I’ve only got ddns from Dynu.com with the name: myname.mywire.org. I don’t know if I can change the name servers with Dynu.com.
Or do I need to purchase a domain name somewhere and the dynamic DNS from Dynu.com is not enough?
I have downloaded the certificate from Nginx and imported it to TrueNas providing the certificate and private key without the passphrase.
Should I edit my Nextcloud instance to use this certificate?
The page is still not available and I got stuck ![]()
First I would like to have a secure connection from outside of my network. Am I doing something wrong, missing anything?
I appreciate your help.
Here’s what I do. I have a pfSense firewall device, so if you have something different you may need to adapt. When it comes to docker I don’t use the TrueNAS apps function. I have my own docker compose file that I use to set up Nextcloud (which I would be happy to share), and I just bind mount to my TrueNAS data sets. I also took an unusual route on how to handle ports. I set the TrueNAS web interface ports to 8080 and 8443, so that I could use the standard port 80 and port 443 in my Nginx Proxy Manager config. You don’t have to do all that, but you may need to adapt my approach to fit your setup.
SO, with all that said, first off you need to buy a domain if you want to use cloudflare tunnels to expose a service externally. But they are cheap, and if you buy one through Cloudflare you will not have to go through a lot of rigamarole to set the name servers to Cloudflare nameservers. I think I pay 9.99/year for my .cc domain and slightly more for my .com domains.
In my Nextcloud I have my domain set to nextcloud.mydomain.com. In Nginx I have a proxy host set from my TrueNAS IP and port 9080 to nextcloud.mydomain.com. You would make that port 30027 in your setup
In my PfSense box, I have my DNS resolver set to local first, then to go out to cloudflare if the host isn’t in the local resolver. I also have a host over ride set so that if I try to resolve nextcloud.mydomain.com it points to the IP of TrueNAS box, where Nginx is running. This part may be tricky for you, if you aren’t using standard port 80/443 for Nginx, but I think you can adjust here as needed.
In my Cloudflare dashboard, under zero trust/networks/tunnels I go into the config for my tunnel. Under the “public hostname” tab I have an entry for my public hostname as nextcloud.mydomain.com and the second line where it says “service” points to HTTPS://nextcloud.mydomain.com
Getting certificates for Nginx is another story. You can google how to do a DNS challenge on cloudflare with Nginx (which you must do since you are not exposing any ports). I do get Let’s Encrypt certs for all of my internal services, so that my traffic is end to end encrypted. You don’t need to worry about certs externally as the Cloudflare tunnel takes care of that automatically.
Please review what I did:
-
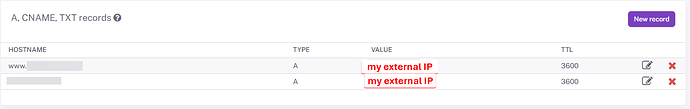
Bought a domain name from a local registrar. Next to the CNAME record, there is the default IP address (don’t know if that should be altered, I assume, its their IP). The provider doesn’t seem to have DDNS service, so I used Dynu.com’s with my own domain name.
I installed DDNS updater application on TrueNAS with my domain name through Dynu. Although the updater itself says on the webUI success, the application status keeps displaying “deploying”. -
Setup port forwarding on my router from external port 80 to 30021 - nginx HTTP, and 443 to 30022 - nginx https.
-
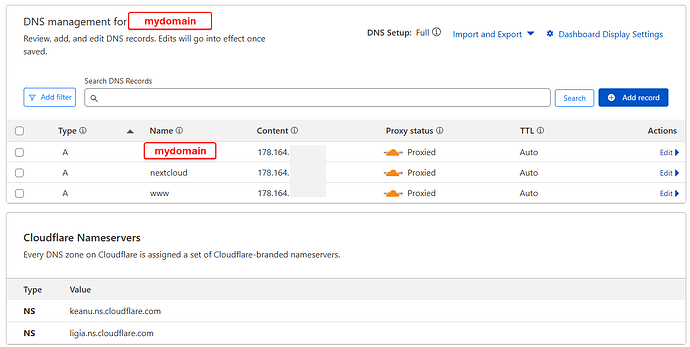
Setup a Cloudflare tunnel with a token. I tried public hostname with nextcloud.mydomain - it was a DNS error even when I added nextcloud as an A record on my DNS zone settings of my domain, so I left only mydomain and the service https://nextcloud.mydomain.
-
I have installed Nginx Proxy manager - created a SSL certificate - Let’s Encrypt with mydomain and Cloudflare token.
-
Installed Nextcloud leaving the Host field empty but setting the environment variable to OVERWRITEHOST - value: nextcloud.mydomain. At the certificate option I chose ‘truenas_default’ (this was the recommended) and also tried without the ‘truenas_default’.
-
Nginx Proxy manager: created a proxy host for Nextcloud. Domain name: nextcloud.mydomain. As I installed Nextcloud with certificate, I chose https and forward port 30027 (nextcloud default port). The SSL certificate is the one from earlier with *.mydomain and mydomain and ForceSSL, etc turned ON. The status is online and the SSL certificate is in use. Do I need to download and import it to the TrueNAS certificates?
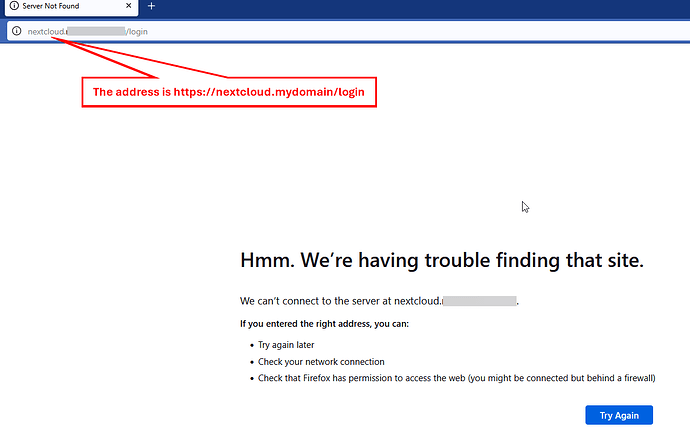
When I open the application URL, loads http://nextcloud.mydomain and the error is the website cannot be reached.
Am I missing something here? I have tried to follow the advise I was given but I might be dummy.
Thank you again for the guidance in advance.
Update: I have taken out Dynu.com from the story and setup Cloudflare DDNS based on this: Cloudflare DDNS Setup on SCALE 24.10.2
Seems to be working for DDNS.
Still struggling with the other parts.
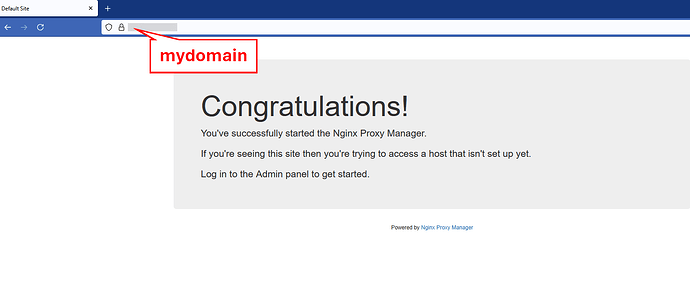
When I open mydomain in a browser:
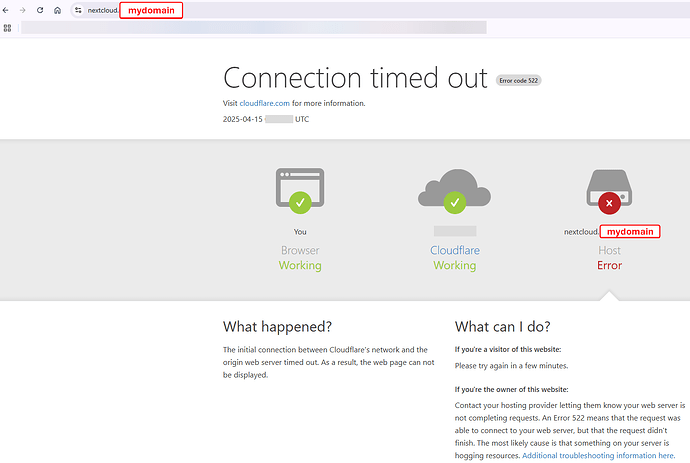
But when I click on the WebUI link on Nextcloud I’m still getting this:
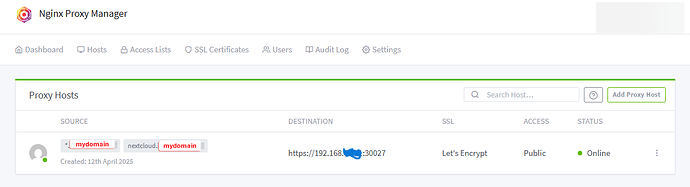
My settings in Ngnix are these:
Nextcloud got installed with the hostname: nextcloud.mydomain and with ‘truenas_default’ Certificate
And these are the settings with my domain registrar:
Cloudflare settings for domain and tunnel:
Here at the public hostname section it does not let me set subdomain to nextcloud.
What’s wrong with what I’m doing?
Sorry for the dumb questions but I do this the first time and appreciate any help showing to the right direction.
There’s a lot to unpack in your last couple of posts. I will try my best to help. First, if you are using a Cloudflare tunnel, the Cloudflare DNS name servers need to be used for your external domain. So it doesn’t matter where you purchase your domain, but Cloudlfare has to do the DNS for it. See here Transfer your domain to Cloudflare · Cloudflare Registrar docs
Second, the point of using Cloudflare tunnels is that you don’t have to use DDNS or port forwarding any more. What kind of router/firewall do you use?
Third, you will not be able to generate a token for a Let’s Encrypt DNS challenge until you migrate your name servers to Cloudflare
SO…first thing you need to correct is moving the name servers for your domain to Cloudflare, and report back when you are successful.
Hi,
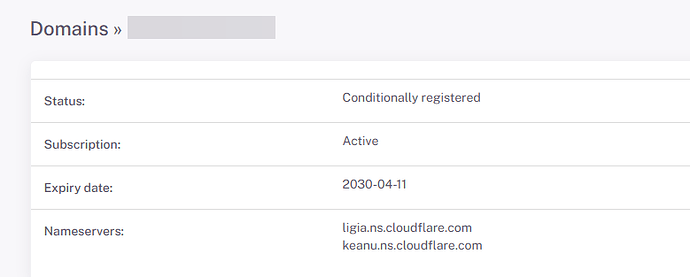
I have had already changed my nameservers on my registrar’s page to the ones to use Cloudflare:
If this is not enough then, I’ll initiate the transfer to Cloudflare. I assumed with DNS setup showing full as on the screenshots that my setup is complete.
I also created the token somehow like this in this guide:
The status of the Token is like this:
The screenshots about the Ngnix settings had already been attached.
If this is still not correct, then I’ll transfer the domain to Cloudflare.
My home router is a Tp-link Archer A9
Thank you for checking my issue.
I have checked my domain name with Network Tools: DNS,IP,Email and it reports that my DNS hosting provider is Cloudflare.
Is that enough for moving forward or should I request a domain name transfer?
Hi,
With the above settings I managed to get to the point where my browser displays the following:
The connection type displays as secure, at least!
So, I assume the connection from outside should work properly and the problem now is inside at least from the error code 522.
My Ngnix Proxy Manager settings are the followings:
Proxy host:
- domain names: *.mydomain, mydomain, nextcloud.mydomain
- scheme: https; server ip; 30027 (nextcloud port)
- only block common exploits is turned on
- SSL certificate: *.mydomain, mydomain
- all the settings turned on: force SSL, HTTP/2 support, HSTS enabled, HSTS subdomains
- Status is Online, access: public
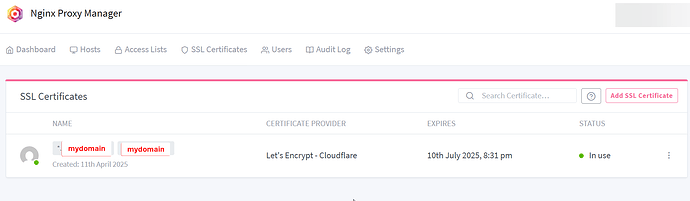
SSL certificates:
- Let’s Encrypt certificate is setup with cloudflare token with the domain names: *.mydomain, mydomain and the certificate’s status shows “in use”.
Nextcloud has been installed with the following settings:
- Host left blank
- Additional environment variable: OVERWRITEHOST - value: nextcloud.mydomain
- Certificate ID: ‘truenas_default’ certificate ; Use diffferent port for URL rewrites (checked) → port: 443
Can you help me further? @Louie1961 do you have any idea?
Thank you.
Hi,
My setup currently:
Truenas Scale: ElectricEel-24.10.2.1
Tp-link router - no port forwarding setup
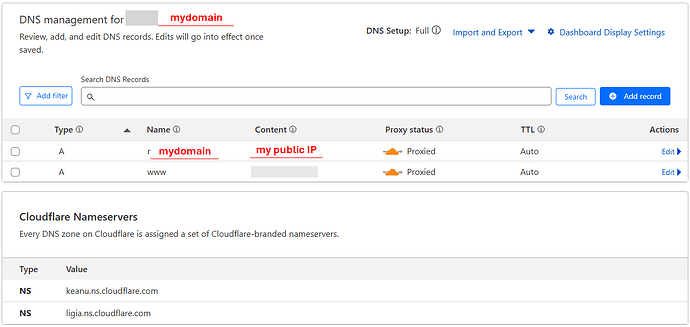
Domain from a registrar but managed on Cludflare:
DNSSec not enabled
Mydomain is using automatic SSL/TLS. Encryption mode is set to Cloudflare’s recommendation.
I have created a Cloudflare tunnel to TrueNAS - status healty
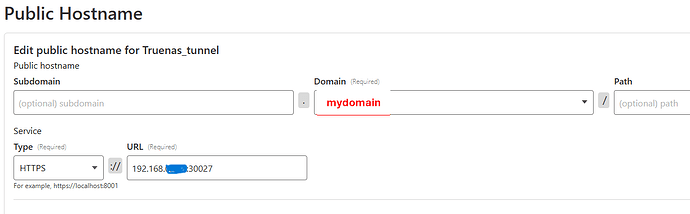
Public hostname: (NO subdomain) - mydomain
Service: HTTPS://192.168.x.x:30022 - Ngnix port for 443 (tried also with Nextcloud port: 30027)
Cloudflared is running on TrueNAS
Nginx Proxy Manager (App Version: 2.12.3; Version: 1.1.14)
My Ngnix Proxy Manager settings are the followings:
Proxy host:
- domain names: *.mydomain, mydomain, nextcloud.mydomain
- scheme: https; server ip; 30027 (nextcloud port)
- only block common exploits is turned on
- SSL certificate: *.mydomain, mydomain
- all the settings turned on: force SSL, HTTP/2 support, HSTS enabled, HSTS subdomains (experimented with setting these off - no luck)
- Stauts is Online, access: public
SSL certificate: - Let’s Encrypt certificate is setup with Cloudflare token (DNS challenge) with the domain names: *.mydomain, mydomain and the certificate’s status shows “in use”.
Nextcloud (App Version: 31.0.2; Version: 1.6.18)
Nextcloud has been installed with the following settings:
- Host left blank
- Additional environment variable: OVERWRITEHOST - value: nextcloud.mydomain
- Certificate ID: ‘truenas_default’ certificate ; Use diffferent port for URL rewrites (checked) → port: 443
- Nextcloud config.php
Automaticly set (no change): ‘overwrite.cli.url’ => ‘https://nextcloud.mydomain’
Automaticly set (no change): ‘overwritehost’ => ‘nextcloud.mydomain’
Automaticly set (no change): ‘overwriteprotocol’ => ‘https’
trusted_domains already contained nextcloud.mydomain
When I don’t set the hostname, then Nextcloud is available from LAN but not from the internet. I tried with different installation versions but without luck.
Generally I receive the following error, at least when tried with https then it does not display “insecure connection”:
Please help me further, I’m stuck.
Any help is appreciated.
Thank you.
Sorry for the delay in getting back to you. I think you have too many moving parts here that you are trying to solve for all at once. I was never any good at multivariable calculus! ![]()
If possible, can you set up a simple VM on some other computer besides your TrueNAS machine? Or even a bare metal install on another computer or even a raspberry Pi. Just something to connect your Cloudflare tunnel to for testing. I would install something simple on it like an apache or Nginx web server, just to see if you can get the Cloudflare tunnel to pass it out to the web at your domain address. Don’t bother configuring the web server, just using the default welcome page will be fine. My point being to isolate to solving one problem at a time. Once you can get the tunnel working outside of TrueNAS, then see if you can get it working with TrueNAS, but without the reverse proxy. Just point the tunnel to the IP address of the TrueNAS and the port number of a container you want to use as a test case. Once you get that working, then we can tackle using a reverse proxy. TrueNAS makes things complicated because they want to use port 80 and 443 for the TrueNAS web interface, and your reverse proxy wants to use those same ports as well.
See if you can get a tunnel working as your first step and report back.