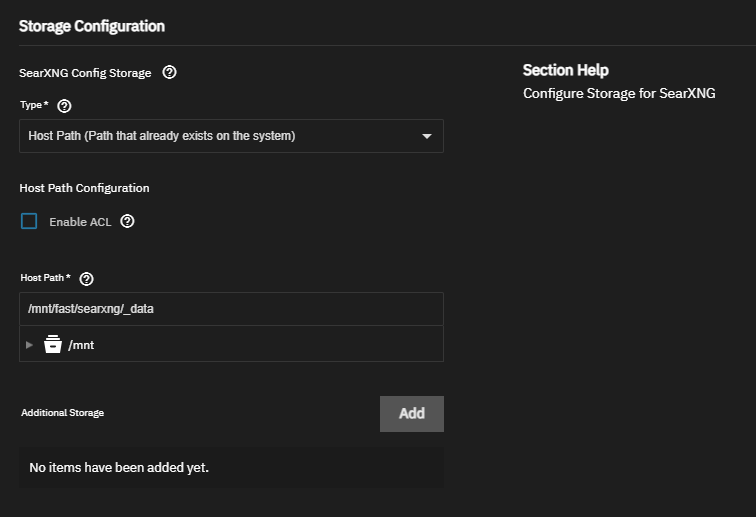
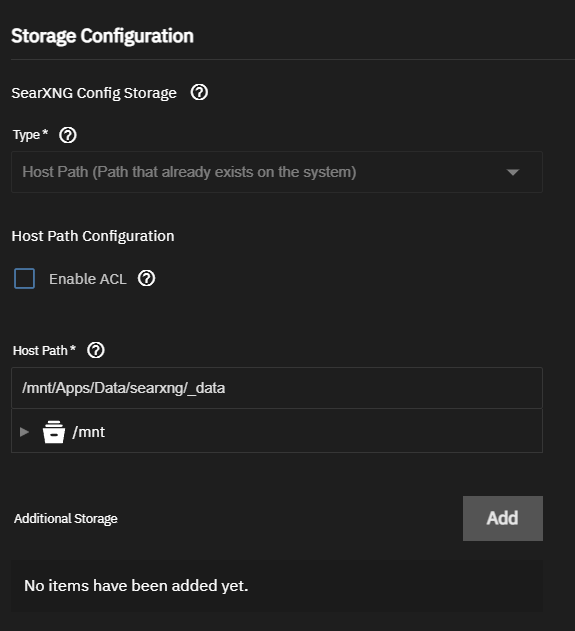
I looked at the process list to see what processes the container uses and as which user. I use ps auxf or htop to do that. You can also see the processes of a single container using sudo docker top ix-searxng-searxng-1 (where ix-searxng-searxng-1 is the container name or id, which can be taken from sudo docker ps):
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1496186 0.0 0.0 848 256 ? Ss Nov18 0:01 \_ /sbin/tini -- /usr/local/searxng/dockerfiles/docker-entrypoint.sh
977 1496226 0.0 0.0 20108 8832 ? S Nov18 0:02 \_ uWSGI master
...
This only works if the container isn’t crashing (which it didn’t in my cause).
In general, if you use the ix app catalog, most containers should run as user/group 999:999. If you launch custom apps you can specify yourself as which user the containers runs as (this doesn’t always work if the container has special needs or isn’t well designed).
Some containers, such as SearXNG, run a process as root and run child processes as a different user. This is the “old” style of running applications which isn’t ideal for containerization.
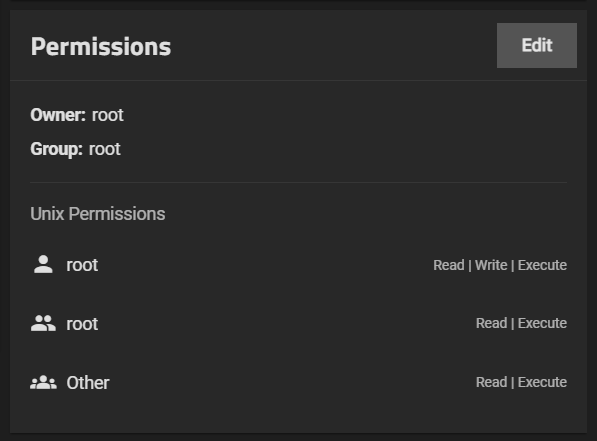
There is no issue with using ACL and adding user 977 to it.
I never used the ACL option in the host path setting, I don’t know what that does yet. Docker itself doesn’t have any file-system ACL options - at least I’ve never seen one in all the years I’ve used docker.
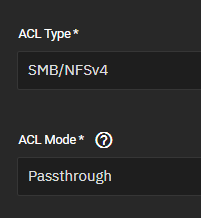
I use ACL Type Off in the dataset settings. In a linux application server you typically won’t find ACLs being used. They’re mainly used for file sharing application (SMB/NFS). It’s not bad if you use them, but it does add a layer of complexity.
Without ACL, the normal posix permissions (not to be confused with posix ACL) will be used. These are the -rw-r--r-- root root stuff you’ll find often in various tools and outputs. You can easily display that in a table and get a overview over the permissions of every file.
Most linux programs only know how to deal with with posix permissions, and will use chmod / chown / umask to manage them.
If you use ACL (either posix acl or nfs4acl) there will be compatibility layer to convert posix permissions and acl (back and forth). This can be pretty complex - it’s why you have a ACL Mode with four possible options if enable ACL in the dataset options.
In the end, I’m just used to posix permissions after decades of managing linux servers. So that’s what I prefer (for non-file sharing purposes!)