Problem/Justification
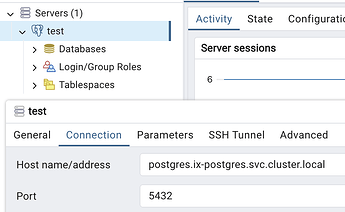
In TrueNAS SCALE 24.04, it was possible for apps to communicate with each other via cluster.local domain names since they were all on the same network. For example, I use the Nginx Proxy Manager app to reverse proxy to another app on the same TrueNAS machine by using its internal domain name, such as http://immich.ix-immich.svc.cluster.local:30041.
In 24.10, this is no longer possible if using the default apps catalog since each app has its own Docker network that is not shared with other apps. Users may work around this by referencing the TrueNAS host’s IP or hostname in place of the previously-used *.cluster.local name, but this creates a dependency between the app and the host and requires the user to expose the necessary port on the host, which may not always be desirable. Another possible way is by using a custom docker-compose YAML file.
Impact
As it currently stands, apps that were once able to communicate with each other are no longer able to. In addition to the reverse proxy use case above, this type of functionality is useful for apps like Sonarr, Radarr, and Prowlarr which communicate with each other and with download clients. I imagine this is a very popular use case for TrueNAS users.
Allowing apps to easily communicate with each other will ease disruption created by the k8s → Docker migration for users upgrading to 24.10 (myself included).
User Story
I can see two possible implementations of this feature.
Implementation 1: All apps share a network
This is most similar to how it worked in 24.04. All apps could simply share a network and all users need to do is change usages of the *.cluster.local names to their Docker network counterpart. For example, immich.ix-immich.svc.cluster.local would become ix-immich-immich-1.
Implementation 2: User-defined networks
By default, apps will only be part of its own network (as the situation is right now). Users will be able to create their own network from the Apps UI or CLI and configure apps to be part of these networks.
This is a slightly more secure option since it facilitates the principle of least privilege, allowing users to dictate which apps can and can’t connect to one another. But it is also slightly more effort.
For a clean K8S → Docker migration, I think it makes sense to work on Implementation 1 as a first pass, then save Implementation 2 for a larger release.