@kris - Is there any desire from IX to officially take over maintenance of jailmaker?
Do you find yourself missing jails? Does the thought of unmaintained jail managers keep you up at night? …Try TrueNAS CORE today; it has a jail manager built right in!
You know, Core’s Jails are not flawless.
Apparently iocage only just received a new maintainer.
And in other news at least 4 people have put their hands up to maintain Jailmaker.
Quit chucking stones in glass houses.
And CORE doesn’t seem to like AM5 in it’s current state … ![]()
You sound angry? Your response is a bit off-topic to my point but I’m not sure I’d call FreeBSD Jails a ‘glass house’. I think that after all these years they would be more of a stone walled castle at this point. However, I guess if we’re speaking in adages here’s another: “a bird in the hand is worth two in the bush” (meaning: maybe use Core–jails–whilst options settle in SCALE).
But seriously, I’m a bit confused by your response (or, I guess, your apparent anger towards it). I never said CORE’s jails were flawless. I was only pointing out (with a bit of humor) that there are other TrueNAS options available (what’s wrong with that?).
Okay? I’m actually not sure what to say to that. …“The UI has themes.”
IF you run an AM5 setup , like I am currently, CORE won’t even boot
I “upgraded” my parts and went to boot back into CORE and got stuck on an “AMDsomething” during boot and through using some Google-Fu … found out it was because the version of FreeBSD that the latest Core is based on doesn’t have drivers for AM5 (something along those lines)
Soo . .I was forced to prematurely go with SCALE.
Core had been running without issue for years prior. I was going to wait for electric eel before making the switch , but … welp, Dragonfish it is until then
Ah. Yeah well, I’m sorry, but my post wasn’t directed at you personally (your situation may be different than mine, Ricky’s, or hers). Other people besides the forum users can read these posts and each person’s situation is different.
I was speaking in general terms that it might be a safer bet to procrastinate for some. To the “others”, the FreeBSD pkg repository is huge and I’m sure you, more experienced *nix users, can manage to install and config a few things if you absolutely need a “jail manager” now.
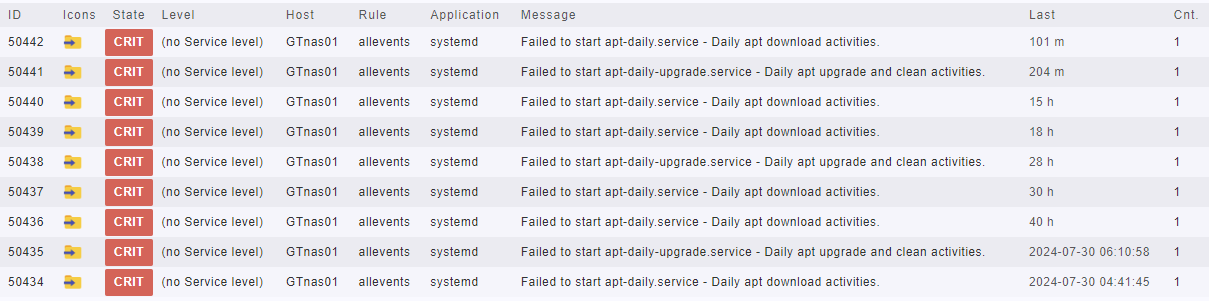
Just a quick message to state I have three TrueNAS boxes, and I run Jailmaker on two of them. The two with Jailmaker were sending syslog messages about these two failed services:
apt-daily.service
apt-daily-upgrade.service
Investigating - these failed services were outside the jail. Inside the jail, they are running fine. Outside the jail, they are borked.
I then went to my third NAS that has yet to see any Jailmaker action and see that these two services are disabled.
I can therefor only assume that somehow Jailmaker enabled apt-daily.service and apt-daily-upgrade.service on the TrueNAS host? Don’t know - my sample size isn’t big enough. Could be coincidence. But anyway it’s just a cosmetic annoyance and I disabled the services all seems good now. TrueNAS is still capable of searching for updates.
BTW I googled and found how to disable these with the following commands:
sudo systemctl disable apt-daily.timer #this is optional
sudo systemctl disable apt-daily.servicesudo systemctl disable apt-daily-upgrade.timer #this is optional
sudo systemctl disable apt-daily-upgrade.service
I rebooted, and the configuration has stuck.
I noticed that my SCALE box without jailmaker only has the services disabled, but not the timers. I figure if you are going to disable the service, you might as well also disable the timer that calls the service. Right? So have decided to disable both timers and services.
That’s all. Hopefully this saves someone a bit of time investigating syslog errors! ![]()
I submitted a big report on it a while back. I think they’ve fixed it in a future version. Maybe ![]()
But nice to confirm that it only happens for some reason on the sandboxy version.
I’m curious how others are handling updates/patching with their jails? This seems like one area that would be advantageous with IX’s built-in apps going to docker. Not having to worry about that as much.
Just using apt to update
On Debian based distributions, you might consider to install the package “unattended-upgrades” to automate the update process. I use it on my Debian servers, it is working well.
I brought my NAS offline yesterday, trying to setup a bridge for my jails while following Stuxs guide (https://youtu.be/uPkoeWUfiHU?si=Xt0L0T1RKr0fC3gm) but luckily it came back over night for no reason.
Right now I have a static ip for my physical interface set, but after creating a bridge my NAS goes offline again. So I cannot continue
Also Stux ended up with a static IP on his bridge, but I just want to use my physical interface with DHCP and then bridge that to my jail. idk why this is so hard
Anyone have an idea how to get this running?
is anyone else having issues with Tailscale getting to run in dockge and macvlan setup?
I just went to install it and it seems to install fine but tailscale up fails. I have tried it under deb and ubuntu and same result for both.
If anyone here has tailscale running on jailmaker i could really appreciate the help lol.
Some people install Tailscale/Wireguard in its own jail using host networking
Others run it in host mode
Others add the right caps
Can I also just say thank you Stux for that super helpful video on how to create jailmaker / dockge. It solved all my problems, and I am seriously thinking of migrating all the k3s apps that work (Plex, Adguard, Qbittorrent) to dockge as a result.
Several really good apps on the Truenas page (Omada Controller, Photoprism) are just broken in the vanilla state so using dockge is really the only option if you want to run apps. I spent so much time trying to figure out how to get Omada and Photoprism to work (they don’t) that I frankly hate k3s now (fairly and unfairly).
Thanks so much Stux, I indeed found these ones. I followed the first before I posted this question, it shows up in Tailscale portal, but I am unable to acces Lan through this tunnel.
Hello, I’m having a little bit of trouble with user name spacing and file access based on group.
I need to pass /dev/dri/renderD128 to the container to allow hardware decoding.
Permission look like this:
ls -l /dev/dri/renderD128
crw-rw---- 1 root render 226, 128 Jul 31 10:09 /dev/dri/renderD128
Since I run my jail with user name spacing, I added the jail root user as a user on the host.
This works and file created by the user in the jail are correctly mapped to the user on the host.
I’ve added that user to the group render which has rw access.
if I su jailuser on the host and try to access the file it works.
However inside the jail I get Permission Denied.
If I change the owner on the host to be the jailuser, it works…
If I change the permission to 666 and leave the owner as root on the it also works…
Any idea why the jailuser would not have access when within the jail when its a member of the render group?
Thanks