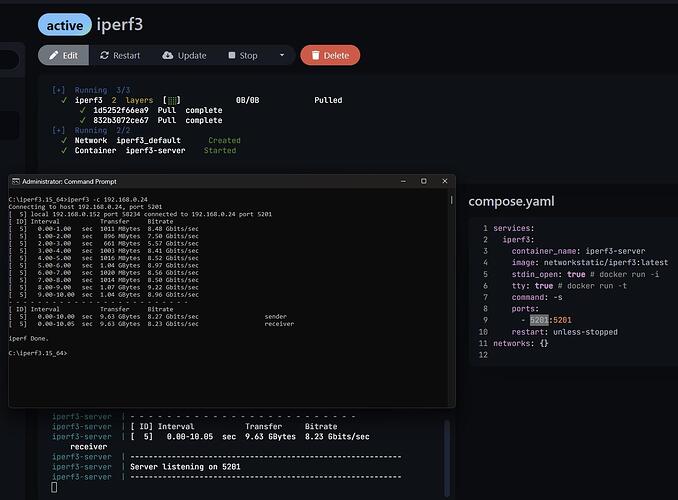
been testing deploying containers
example
services:
syncthing:
image: lscr.io/linuxserver/syncthing:latest
container_name: syncthing
hostname: syncthing #optional
environment:
- PUID=1000
- PGID=999
- TZ=newyork
volumes:
- /mnt/docker/data/syncthing/appdata/config:/config
ports:
- 8384:8384
- 22000:22000/tcp
- 22000:22000/udp
- 21027:21027/udp
restart: unless-stopped
networks: {}
i had created a docker user in truenas
1000:999
UID:GID
seems to work. doing further testing
Noted that when dockge deployed, the owner is still root.
i use syncthing to sync between android mobile to nas to backup
- keepass database
- aegis 2fa database
both encrypted of course
refer to this video how to set that up
*update
ok i got this setup. it’s working and using the docker user in compose environment and seems to work.
so i guess i don’t have to use 0:0 for deploying dockers unless there is a special reason to do so.
So what’s nice about this setup?
For starters keepassdx is an android app for locking/unlocking/access to your keepass database to access your credentials. so on your android you can access stuff using credentials through that app. It can be unlocked with fingerprint making it convenient and secure.
It’s not just keepass. It can also backup aegis which is a 2fa app (WAY better than google authenticator). Aegis can do local encrypted backups which can be easily restored. This is what you will be backing up/sync using syncthings to keep a copy on both your mobile android and your truenas.
It also works great on the go and does not require the cloud.
Once you are back home for the day, syncthings will reach out to your nas on the network and sync ANY changes that happened automatically.
So no, you don’t crappy solutions like lastpass and those paid subscription password managers.
The alternative to keepass is something like vaultwarden. But to use this, you must have a working https cert for it to work. Otherwise the android client will complain and you cannot use it. keep that in mind.
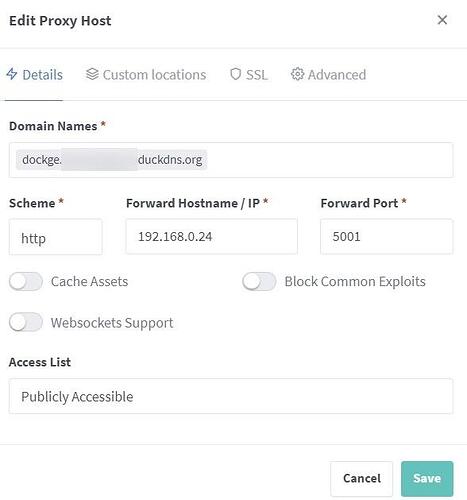
and the cherry ontop, i setup the local domain via nginxproxymanager
https://syncthing.yourdomain.duckdns.org/
going to keep the ball rolling and add more dockers