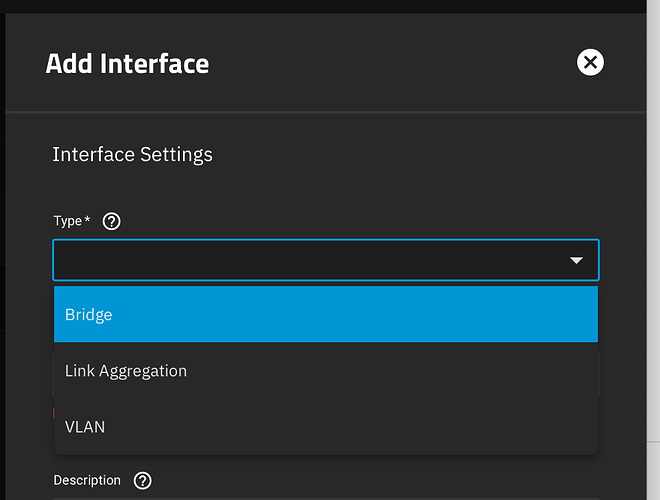
TrueNAS should support creating and configuring a MACVLAN interface when using “Add Interface”.
Ie, MACVLAN should be an option in this menu.
This would prevent complicated CLI scripting in order to create macvlan interfaces and configuring routing tables to allow docker macvlan<->host communication.
Macvlan is supported by the Linux kernel and is a well known Linux network type
It behaves a bit like a cross between a VLAN and a Bridge.
The underlying command line to create the macvlan interface on the host is
ip link add macvlan0 link ens3 type macvlan mode bridge
Where macvlan0 is the name of the new interface, and ens3 is the parent interface. bridge is the macvlan mode, the most permissive, should be the default, but would ideally be configurable
The Linux implementation is lightweight and it eliminates the need for using a Linux bridge for sharing host access with jails and virtual machines, and importantly is supported by Docker.
The interface would allow you to pick the parent interface, possibly the macvlan mode, as well as an optional VLAN tag.
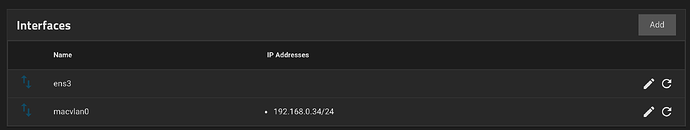
If MACVLAN interfaces could be created and configured, then you would be able to assign an IP address to a macvlan interface, much like how a Bridge network can be assigned at the moment.
For example:
This would mean that Docker macvlan containers would be able to communicate with the host, the same as virtual machines and jails can currently when using a bridge network, as documented in the below links.
YouTube - Setting up a Static IP and Network Bridge
TrueNAS Docs - Accessing NAS from a VM or Apps
For example, the following container which is on the same macvlan network as above
services:
netshoot:
tty: true
image: nicolaka/netshoot
networks:
- macvlan0
networks:
macvlan0:
external: true
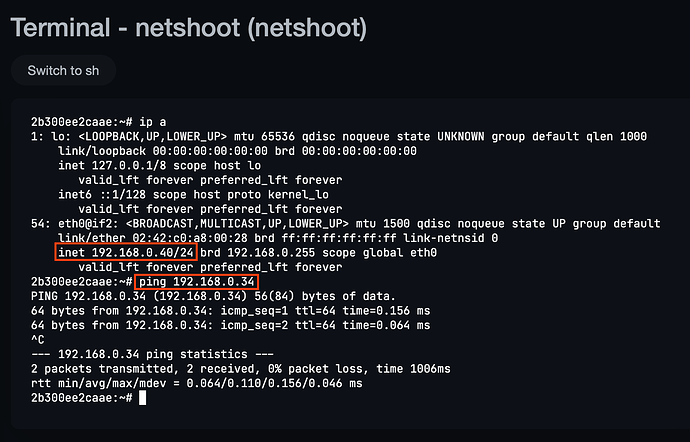
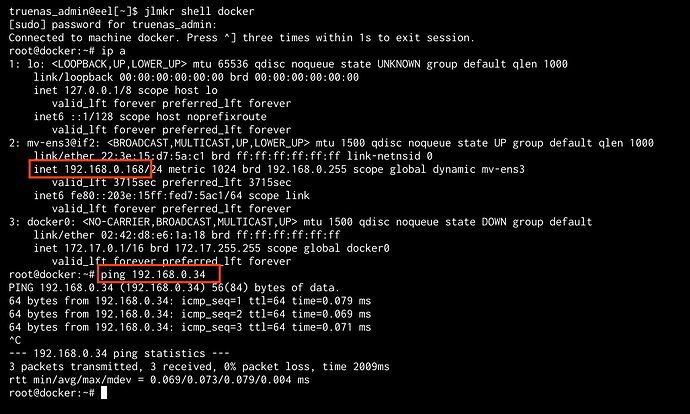
Can easily communicate with the TrueNAS host.
Without performing any custom routing, or command line shenanigans.
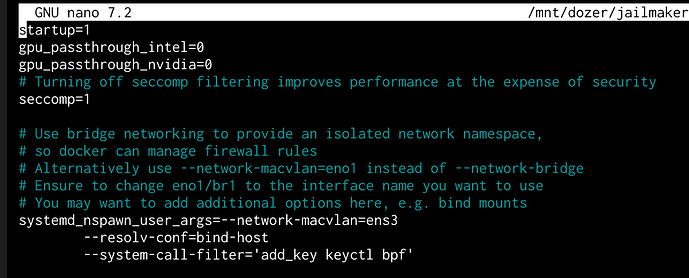
This also means that a Jailmaker jail is able to communicate with the TrueNAS host without using a bridge (note: --network-macvlan rather than --network-bridge) in the config.
Meaning that the Jail can successfully communciate with the host.
Again, not usually possible without using a bridge.
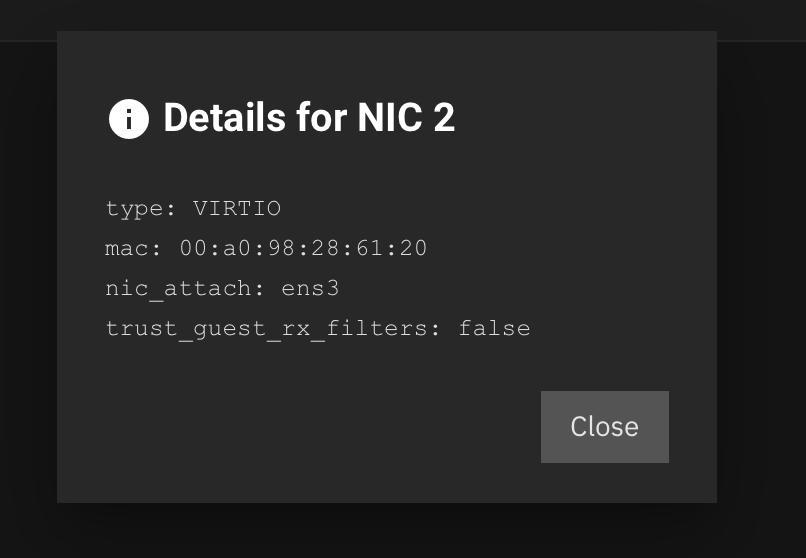
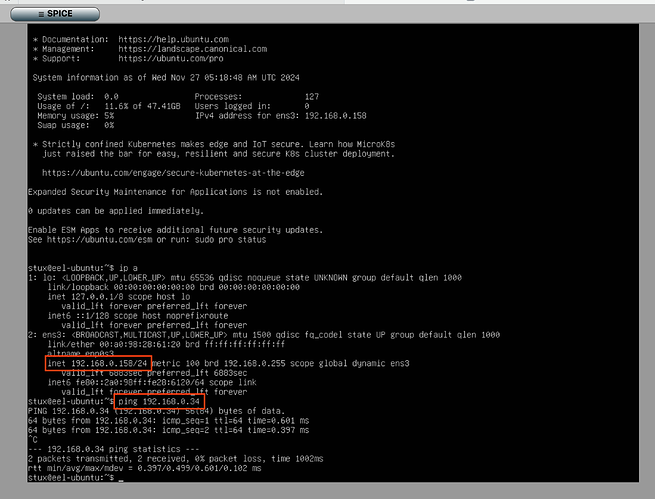
And this also means that a VM guest is able to communicate with the host without using a Bridge.
The VM is configured to use ens3 rather than a Bridge. This translates to a MACVLAN tap.
NOTE: In all examples, the Jail, Container or VM was able to communicate with the LAN, other MACVLAN clients, and the Host without using a Bridge, in a simple fashion, and network performance was also improved by bypassing the Bridge.
DHCP lease acquisition delay is also removed due to there being no need for STP on the MACVLAN bridge-like device.